Overview
This SME-focused Outsourced Development Policy sets clear requirements for secure, contract-controlled software development by third parties. It covers contract obligations, secure coding, asset ownership, and post-project offboarding, ensuring regulatory compliance and risk mitigation even in organizations without dedicated IT or security teams.
SME-Focused Security
Tailored for SMEs without dedicated IT teams, ensuring robust controls and compliance in outsourced development.
Clear Ownership
Mandates contractual clarity on asset ownership and full rights over deliverables and documentation.
Compliant & Auditable
Supports ISO 27001:2022 certification and maintains records for audits, legal, and regulatory needs.
Enforced Secure Practices
Requires secure coding, proper vetting of third-party components, and post-delivery testing.
Read Full Overview
Policy Diagram
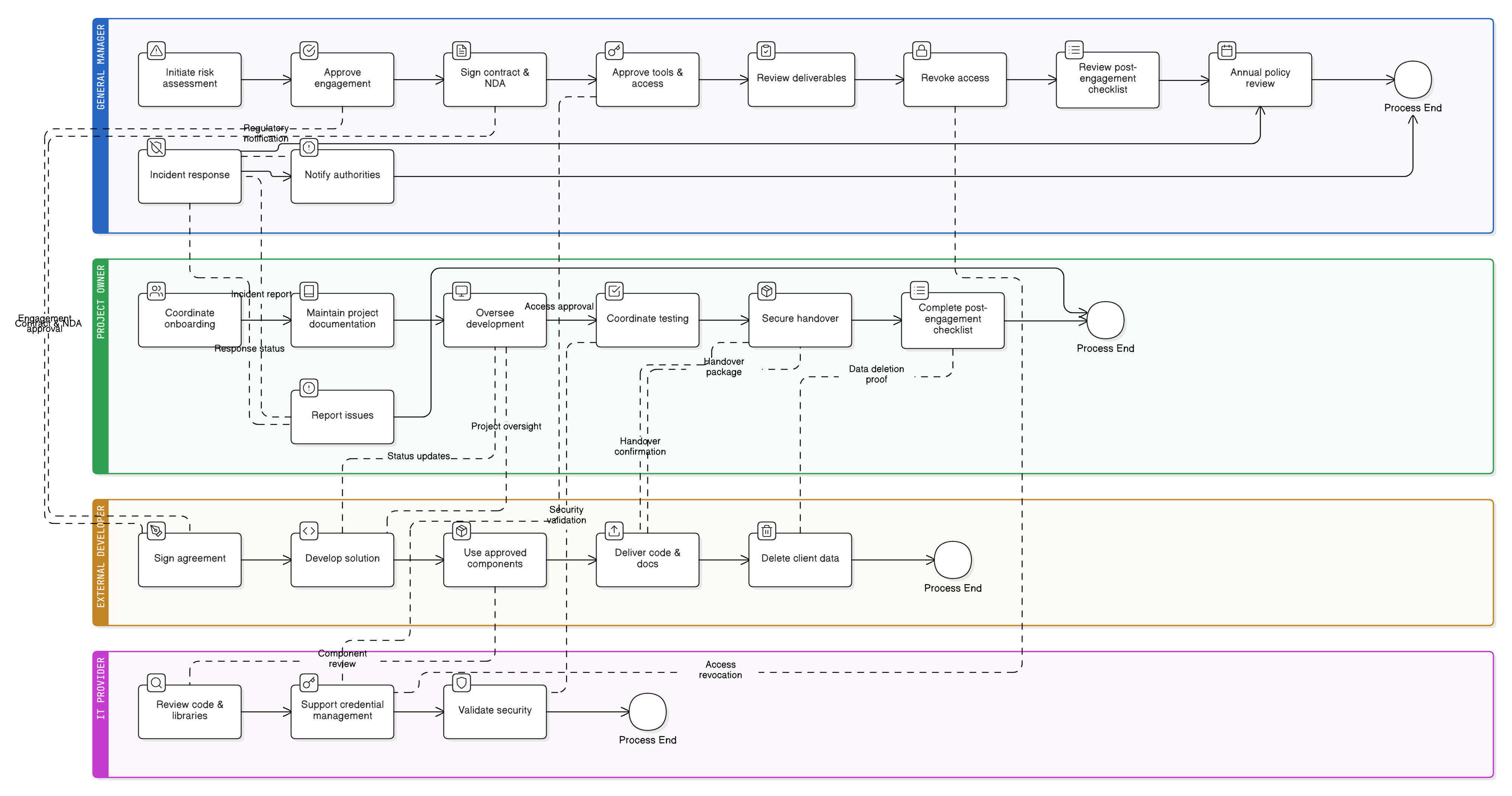
Click diagram to view full size
What's Inside
Scope and Rules for External Development
Mandatory Contracts and NDA Clauses
Secure Coding and Testing Requirements
Access and Credential Management
Ownership, Handover, and Offboarding
Exception and Incident Response Processes
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Clarifies who is responsible for vendor approval, access control, and risk acceptance when using outsourced developers.
Access Control Policy SME
Defines the proper creation, restriction, and termination of user accounts and admin access used during outsourced development.
Information Security Awareness And Training Policy SME
Ensures internal staff understand how to coordinate securely with external developers, including handling credentials and project files.
Data Protection And Privacy Policy SME
Establishes security and legal requirements for handling personal data that may be processed by outsourced developers under GDPR.
Secure Development Policy SME
Specifies how internal and external development must follow secure coding practices and vetting of libraries and frameworks.
Incident Response Policy SME
Required when outsourced development leads to security incidents or vulnerabilities, guiding coordinated investigation and remediation.
About Clarysec Policies - Outsourced Development Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Simple, Role-Based Oversight
Assigns oversight and approval to actual SME roles, like GM and IT Provider, for practical day-to-day control and accountability.
Handover & Offboarding Checklist
Requires signed delivery checklists, code transfer, and proof of data deletion for secure project closure and minimal residual risk.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
