Overview
This SME-focused policy outlines how information security roles, duties, and oversight are assigned and maintained, ensuring compliance and auditability even without a dedicated IT team.
Clear Security Accountability
Roles, duties, and oversight are documented for total clarity and compliance.
SME-Friendly Simplicity
Adapted for organizations without a dedicated IT or security team, empowers managers to stay compliant.
Audit Readiness and Trust
Supports audits, reduces confusion, and fosters customer trust through formal responsibilities.
Read Full Overview
Policy Diagram
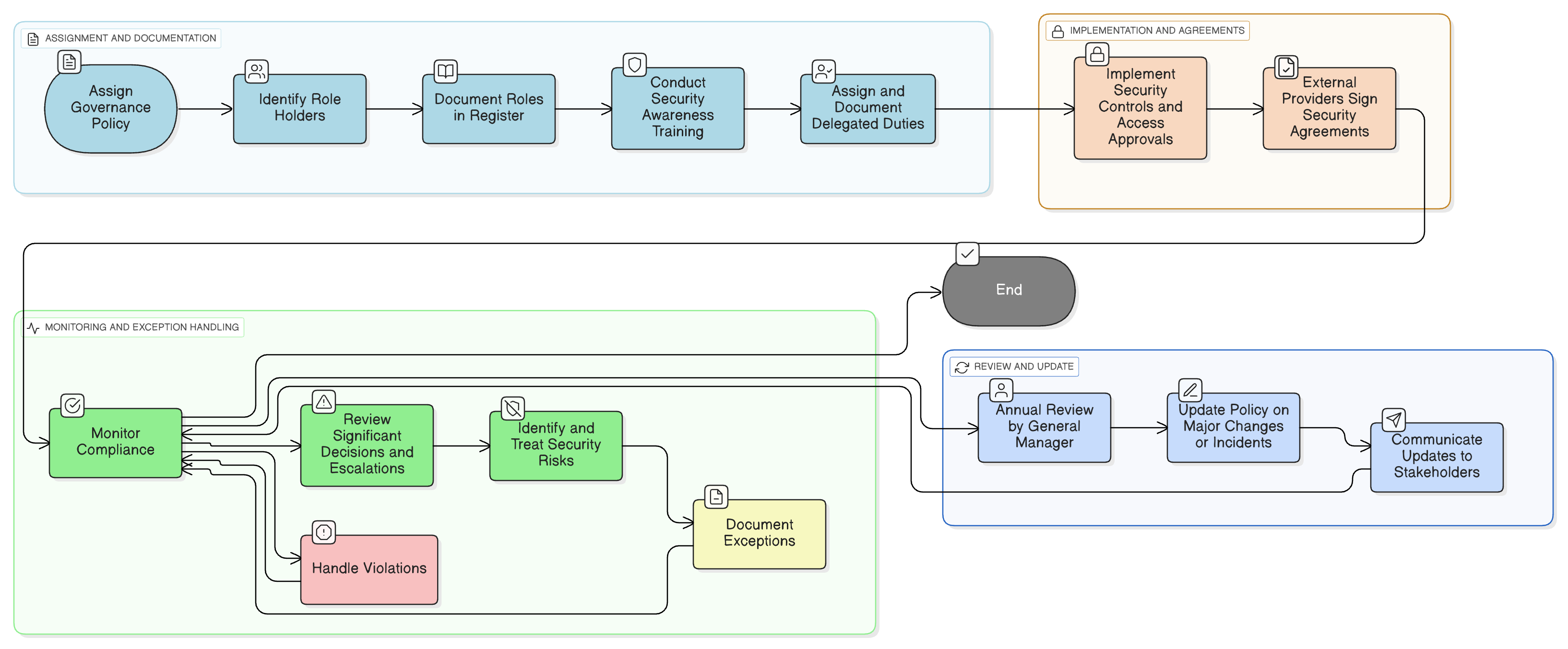
Click diagram to view full size
What's Inside
Scope and Role Definitions
Delegation and Oversight Rules
Responsibilities Register Guidance
Provider Security Obligations
Exception and Escalation Protocols
Review and Communication Processes
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Access Control Policy-SME
Defines how access is granted, managed, and revoked, directly tied to assigned roles and oversight.
Information Security Awareness And Training Policy-SME
Reinforces role-specific responsibilities and expectations.
Data Protection And Privacy Policy-SME
Outlines legal duties under GDPR, which are assigned to roles defined in this governance policy.
Incident Response Policy-SME
Requires defined responsibilities for reporting, escalation, and resolution of incidents.
About Clarysec Policies - Governance Roles and Responsibilities Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Traceable Delegation Process
All delegations and exceptions must be documented and reviewed, ensuring security decisions are always tracked and accountable.
Easy Integration With IT Providers
External IT partners have clear, contractually bound duties, making oversight and escalation simple for SMEs.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
