Overview
This SME-focused policy mandates comprehensive security awareness training for all staff, covering onboarding, annual refreshers, and incident-driven updates, assigning responsibilities to General Manager, HR, and team leads, and ensuring compliance with regulations like ISO/IEC 27001:2022 and GDPR.
Comprehensive Security Training
Covers onboarding, annual refreshers, incident-driven updates, and real-world scenarios to reduce human error.
Role-Based Responsibilities
Clear duties for General Manager, HR, managers, and staff, optimized for SMEs with non-specialist teams.
Easy Compliance Documentation
Training completion and acknowledgments are centrally logged for audits and ISO/IEC 27001:2022 compliance.
Continuous Policy Review
Annual and incident-driven updates keep training relevant to current threats and company needs.
Read Full Overview
Policy Diagram
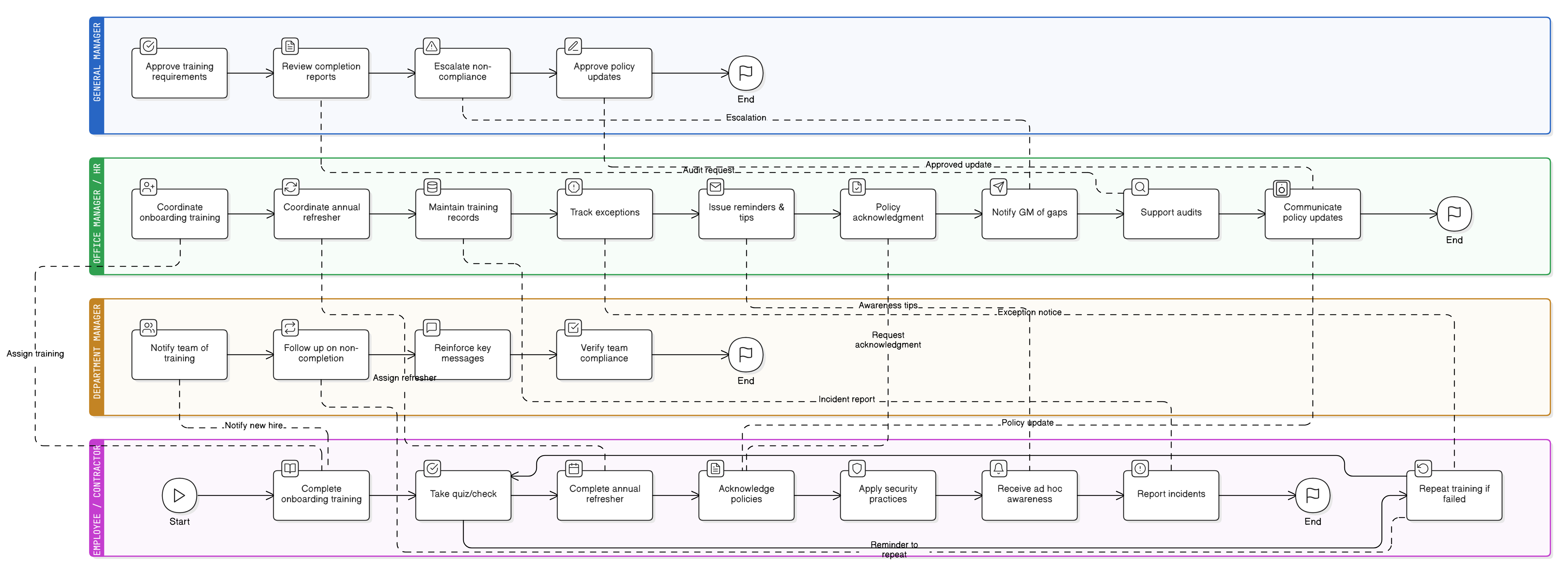
Click diagram to view full size
What's Inside
Scope and Role Coverage
Onboarding and Annual Training Requirements
Event-Driven and Monthly Awareness Activities
Tracking, Documentation, and Audit Requirements
Risk Mitigation and Exceptions Handling
Enforcement and Review Process
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 | |
| EU GDPR |
Article 32Article 39
|
Related Policies
Governance Roles And Responsibilities Policy-SME
Assigns responsibility for training coordination and oversight.
Acceptable Use Policy-SME
Reinforces expectations for behavior addressed in training.
Access Control Policy-SME
Ensures users understand the importance of access security.
Onboarding And Termination Policy-SME
Embeds training into the entry process.
Incident Response Policy-SME
Ensures staff know how to report incidents promptly and correctly.
About Clarysec Policies - Information Security Awareness and Training Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Tailored Awareness Activities
Event-driven briefings and monthly reminders ensure staff are kept informed of new threats and changes.
Exception Handling Support
Flexible scheduling and alternate formats for staff unable to attend, minimizing training gaps and non-compliance risk.
Practical, Role-Appropriate Content
Training materials use plain language and real-life scenarios, directly mapped to SME roles and responsibilities.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
