Overview
The SME Access Control Policy (P04S) defines how access to systems, data, and facilities is managed, ensuring only authorized users gain entry while enforcing the least privilege, and aligning with ISO/IEC 27001:2022. It outlines clear roles, annual reviews, and compliance standards for organizations without dedicated security teams.
Principle of Least Privilege
Limits user access to only what's necessary for job roles, reducing unauthorized access risks.
Clear Role-Based Access
Defines responsibilities for General Manager, IT, managers, and staff for smooth access management.
Annual Review and Audit
Requires yearly access reviews and robust audit trails to ensure ongoing compliance.
BYOD & Physical Access Control
Protects organizational assets across devices and locations, including personal devices and secure areas.
Read Full Overview
Policy Diagram
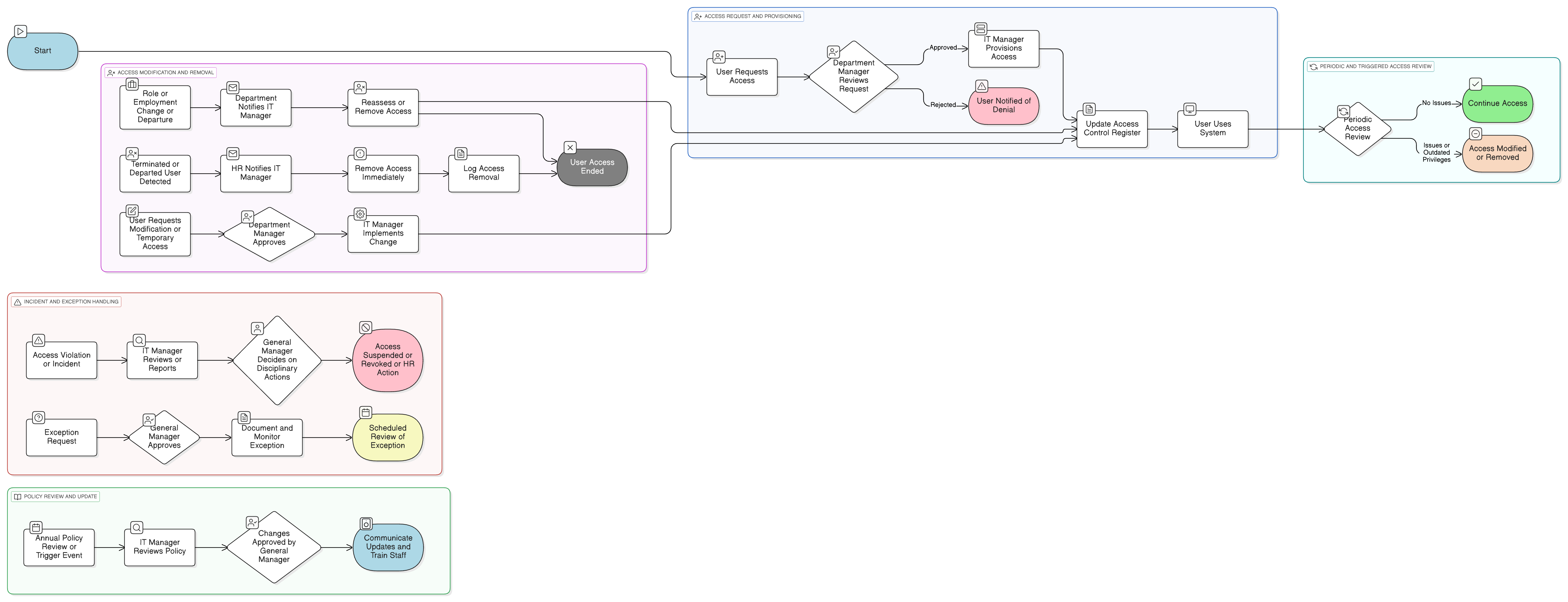
Click diagram to view full size
What's Inside
Scope and Roles of Engagement
User Lifecycle Procedures (Provisioning/Removal)
Periodic Access Review and Audit
Privileged Access Management
BYOD and Physical Access Control Requirements
Exception and Violation Handling
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Acceptable Use Policy-SME
Ensures users understand acceptable behavior with granted access.
Change Management Policy-SME
Ensures access rights are aligned with approved system changes.
Onboarding And Termination Policy-SME
Defines triggering points for provisioning and deprovisioning user access.
Data Protection And Privacy Policy-SME
Ensures access controls align with personal data safeguards.
Incident Response Policy-SME
Defines how access-related incidents (e.g., misuse or breaches) are managed and investigated.
About Clarysec Policies - Access Control Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Access Control Register
Requires secure tracking of all access changes with detailed logs, username, roles, approvals, and timestamps.
Automated and Manual Provisioning
Supports both automated tools and manual templates for account creation, ensuring flexibility for any SME setup.
Exception Handling Process
Deviations must be approved, documented, and risk-monitored, protecting compliance without needless complexity.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
