Overview
This Incident Response Policy outlines how SMEs can efficiently detect, report, and recover from information security incidents, specifying staff roles, third-party requirements, and audit-ready procedures.
SME-Focused & 27001 Compliant
Designed for small businesses with simplified roles to meet ISO/IEC 27001:2022 incident management requirements.
Clear Responsibilities
General Manager-driven oversight ensures timely reporting, containment, and required notifications.
Comprehensive Incident Types
Covers malware, data breaches, phishing, outages, device loss, and accidental disclosures.
Staff Awareness & Training
All staff trained to recognize and report security incidents as part of onboarding and annual refreshers.
Audit-Ready Recordkeeping
Incident logs, reviews, and evidence kept in order for audits and compliance checks.
Read Full Overview
Policy Diagram
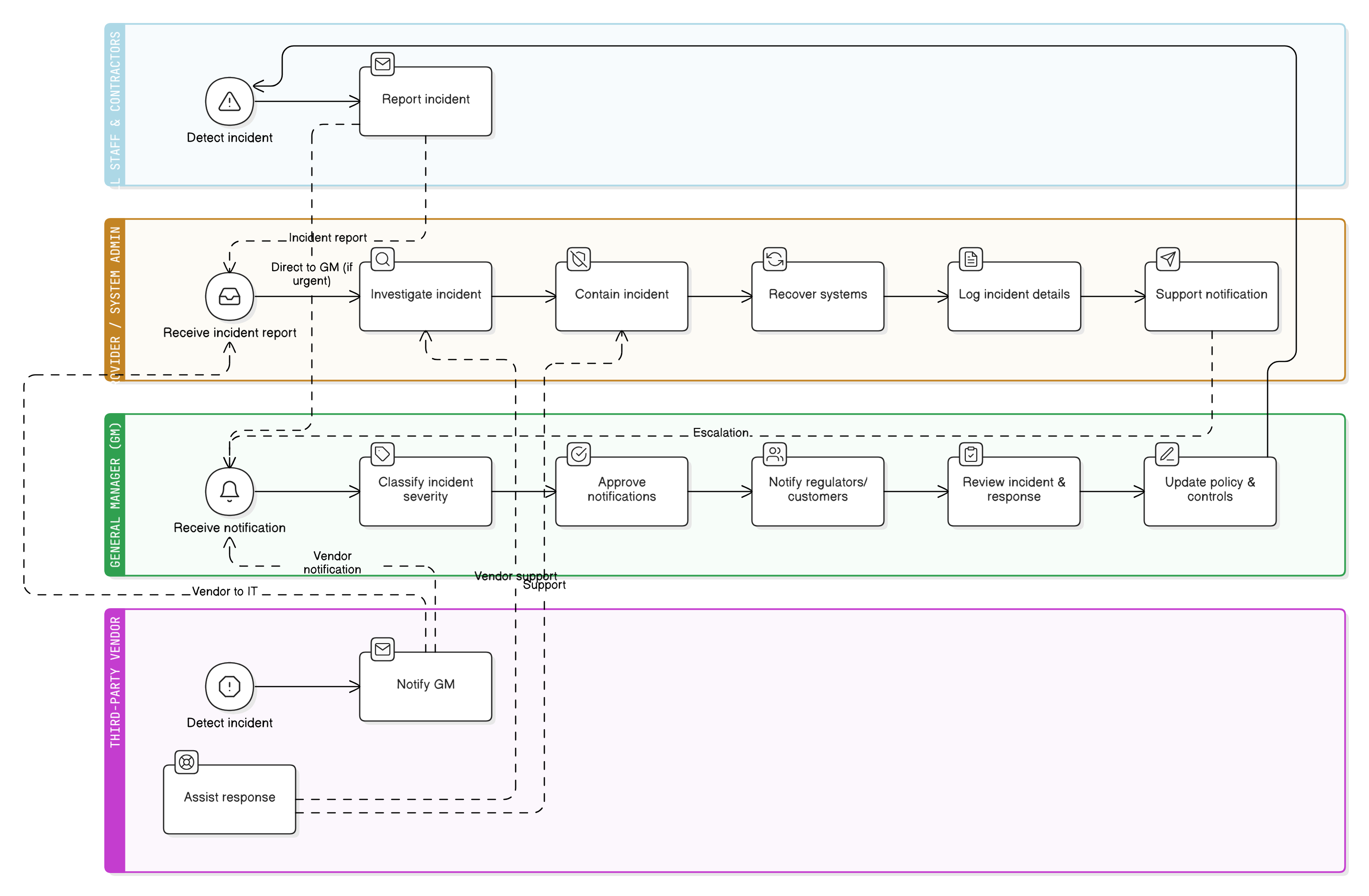
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Incident Detection and Escalation Process
Roles and Responsibilities for SMEs
Third-Party and Supplier Reporting
Incident Log and Recordkeeping Requirements
Compliance, Monitoring, and Enforcement
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Establishes authority and accountability structures for incident detection, reporting, and escalation.
Information Security Policy-SME
Sets the overall expectations for maintaining confidentiality, integrity, and availability during operations, including incident handling.
Access Control Policy-SME
Enables immediate revocation of access rights during incident response actions.
Information Security Awareness And Training Policy-SME
Ensures all employees can identify and report security incidents effectively.
Data Protection And Privacy Policy-SME
Guides legal breach notification procedures under GDPR and supports regulatory compliance during incidents.
Logging And Monitoring Policy-SME
Provides the necessary tools and visibility for detecting, analyzing, and auditing security events.
Evidence Collection And Forensics Policy-SME
Supports investigation and legal defensibility of incident-related actions by guiding proper evidence handling.
About Clarysec Policies - Incident Response Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Rapid Incident Escalation
Incidents must be reported and classified within 1 hour, enabling swift action to minimize damage and regulatory exposure.
Integrated Third-Party Handling
External vendors are bound by the same urgent notification and response process, reducing supplier-related risks.
Root Cause Analysis & Improvement
Post-incident reviews drive ongoing policy updates and corrective actions to prevent future recurrence.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
