Overview
This Data Protection and Privacy Policy (P17S) outlines how SMEs can protect personal data in line with laws and major frameworks, assigning clear roles like General Manager and Privacy Coordinator, detailing secure data handling, risk treatment, and privacy rights management, and ensuring compliance is attainable even without a dedicated security team.
SME-Optimized Data Protection
Guided by simplified roles like General Manager, making compliance accessible for organizations without specialist IT teams.
Comprehensive Legal Coverage
Aligned with GDPR, ISO 27001, NIS2, and DORA to support audit readiness and minimize legal risk.
Clear Responsibilities
Defines roles for GM, Privacy Coordinator, IT, and all staff to ensure accountability throughout the business.
Privacy Rights and Secure Deletion
Ensures timely responses to data requests and mandates secure data disposal processes for compliance.
Read Full Overview
Policy Diagram
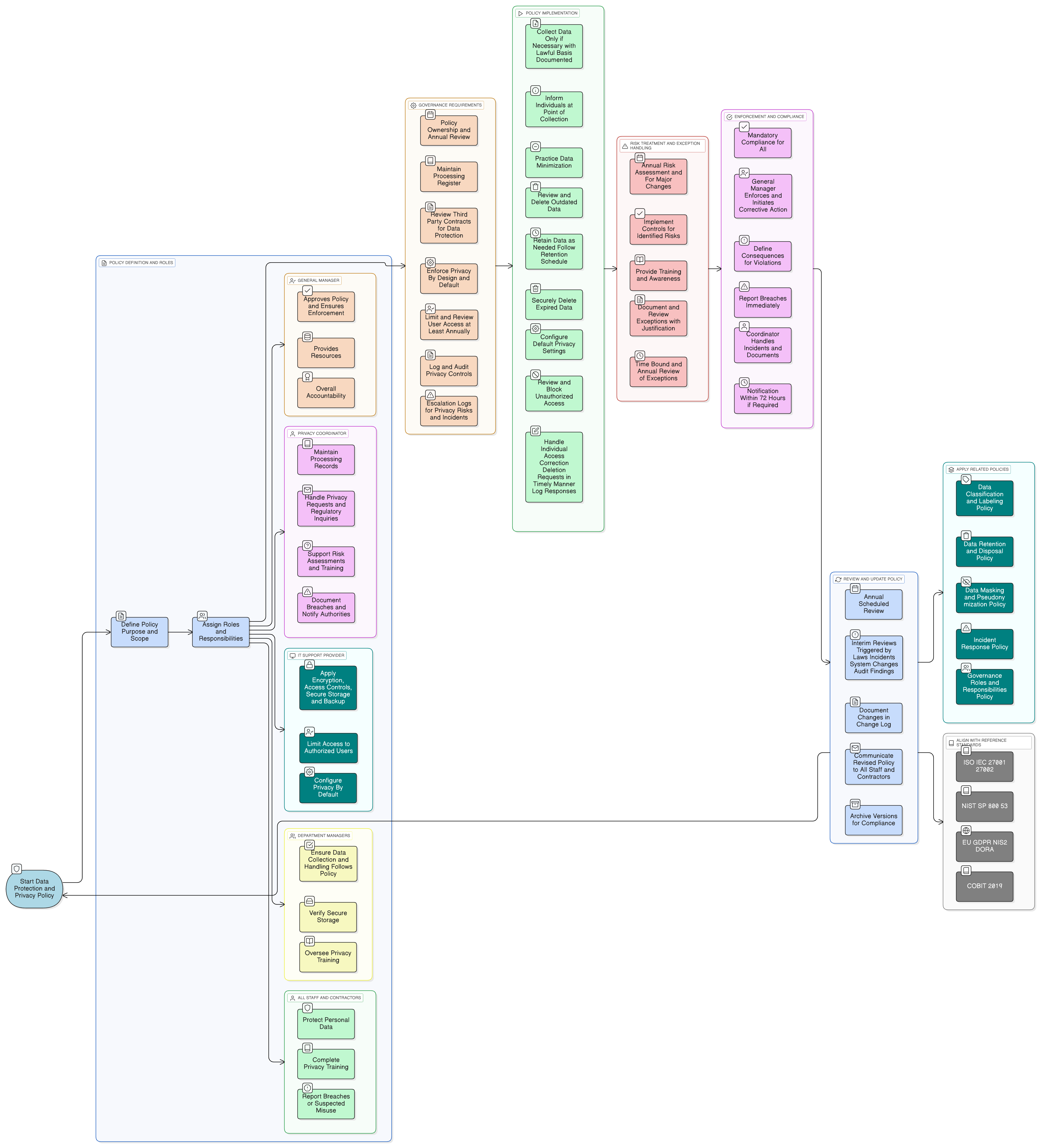
Click diagram to view full size
What's Inside
Scope and Applicability to SMEs
Roles and Responsibilities (GM, Privacy Coordinator)
Privacy Records and Documentation
Risk Mitigation and Exception Handling
Data Retention and Secure Deletion
Response to Individual Rights Requests
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Clarifies the accountability structure and decision-making roles that apply to privacy enforcement and oversight.
Data Classification And Labeling Policy-SME
Ensures that personal data is appropriately classified so privacy protections can be applied based on risk.
Data Retention And Disposal Policy-SME
Provides clear rules for how long personal data must be kept and the secure methods for its disposal once expired.
Data Masking And Pseudonymization Policy-SME
Specifies how personal identifiers must be transformed before data is used in non-production environments or shared externally.
Incident Response Policy-SME
Covers the steps required for responding to data breaches, including notification of regulators and affected individuals within required timelines.
About Clarysec Policies - Data Protection and Privacy Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Audit-Ready Change Log
Maintains documented logs for all policy revisions, ensuring compliance history and traceability for regulators.
Built-In Exception Handling
Structured process for documenting and reviewing deviations, protecting business flexibility while maintaining compliance.
End-to-End Privacy Integration
Designed to operate seamlessly with related SME privacy policies for full data lifecycle coverage.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
