Overview
The Coordinated Vulnerability Disclosure Policy (P39) establishes a formal process for reporting, managing, and disclosing security vulnerabilities, providing a safe and structured channel for external parties while ensuring compliance with NIS2 and international standards.
Clear Reporting Channels
Offers secure channels for external researchers and partners to report vulnerabilities efficiently.
Safe Harbor for Researchers
Protects good-faith reporters from legal action when vulnerabilities are reported responsibly.
Timely Remediation
Sets defined timelines for acknowledgment, triage, and fixing critical vulnerabilities.
Compliant and Transparent
Aligns with NIS2, ISO/IEC 29147, and other best practices for vulnerability disclosure.
Read Full Overview
Policy Diagram
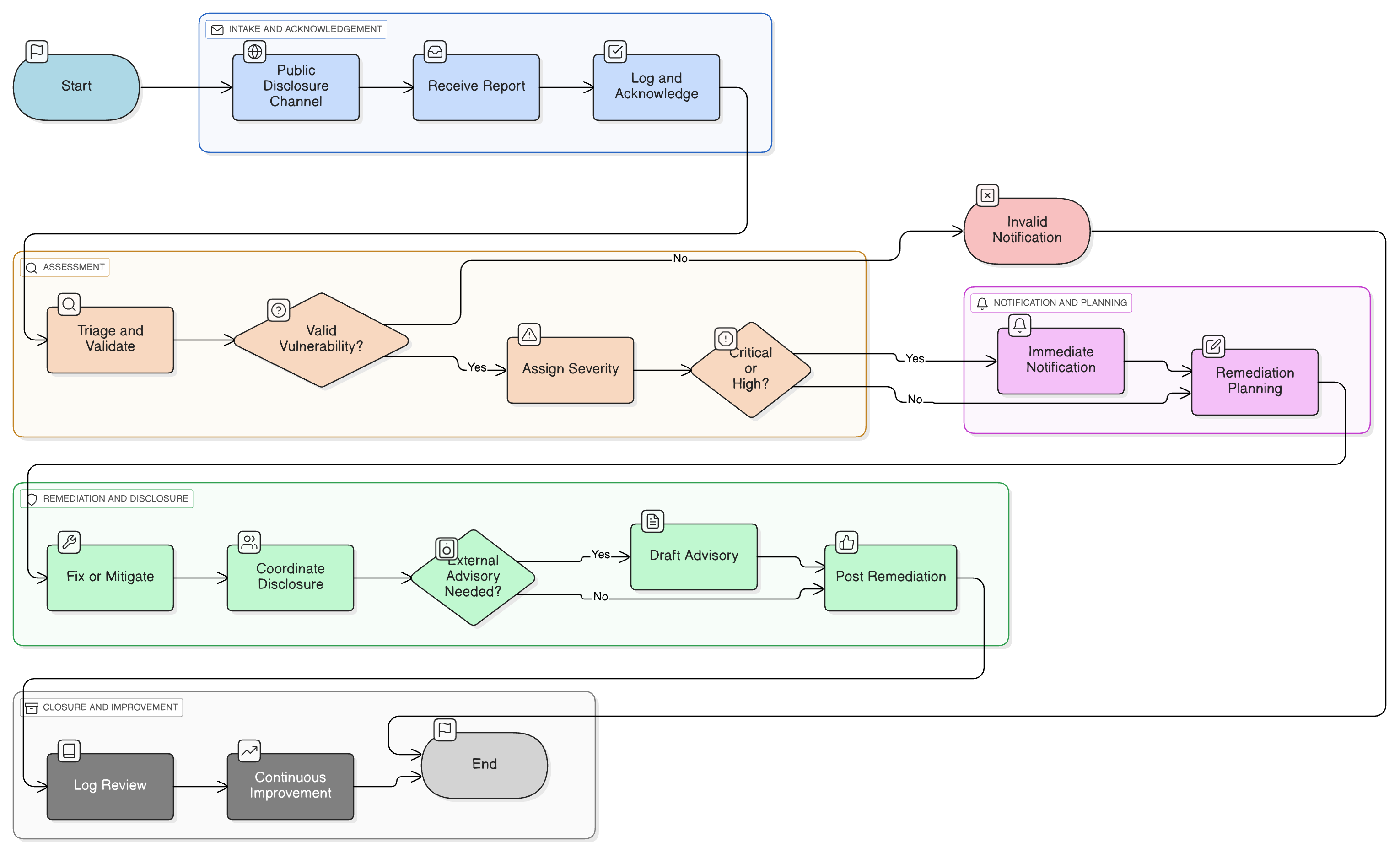
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Vulnerability Submission & Triage Process
Safe Harbor Guidelines
Internal and External Notification Procedures
Disclosure and Communication Protocols
Audit, Metrics, and Policy Review
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy
Management mandate for vulnerability handling and disclosure.
Vulnerability And Patch Management Policy
Internal remediation pipeline linked to CVD intake.
Secure Development Policy
Feeds fixes and SDLC hardening from reported issues.
Application Security Requirements Policy
Ensures products have disclosure-ready security requirements.
Incident Response Policy
Handles active exploitation of disclosed vulnerabilities.
Evidence Collection And Forensics Policy
Preserves artifacts from reported/exploited flaws.
Third Party And Supplier Security Policy
Coordinates disclosures involving supplier components.
Legal And Regulatory Compliance Policy
Governs notification, safe-harbor wording, and publication.
About Clarysec Policies - Coordinated Vulnerability Disclosure Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Coordination with External Parties
Formalizes joint disclosure and remediation steps with reporters, customers, suppliers, and authorities for seamless vulnerability resolution.
Integrated with Key Security Policies
Links vulnerability disclosure directly into secure development, incident response, and evidence collection workflows for full lifecycle coverage.
Continuous Improvement Loop
Every case triggers post-mortem reviews, metrics tracking, and process updates to strengthen future vulnerability responses.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
