Overview
The Evidence Collection and Forensics Policy (P31) provides a detailed, organization-wide framework for managing digital evidence during security incidents, ensuring forensic readiness, evidentiary integrity, regulatory compliance, and legally defensible investigations, aligned with leading international standards.
Forensic Readiness
Defines structured protocols for rapid and secure evidence collection during security incidents.
Evidentiary Integrity
Mandates strict chain of custody, secure storage, and integrity checks to uphold admissibility.
Defined Roles & Escalation
Clear responsibilities for CISO, forensics teams, IT, and legal during investigations and legal escalations.
Regulatory Alignment
Processes comply with standards such as ISO 27001, NIST SP 800-53, GDPR, and DORA.
Read Full Overview
Policy Diagram
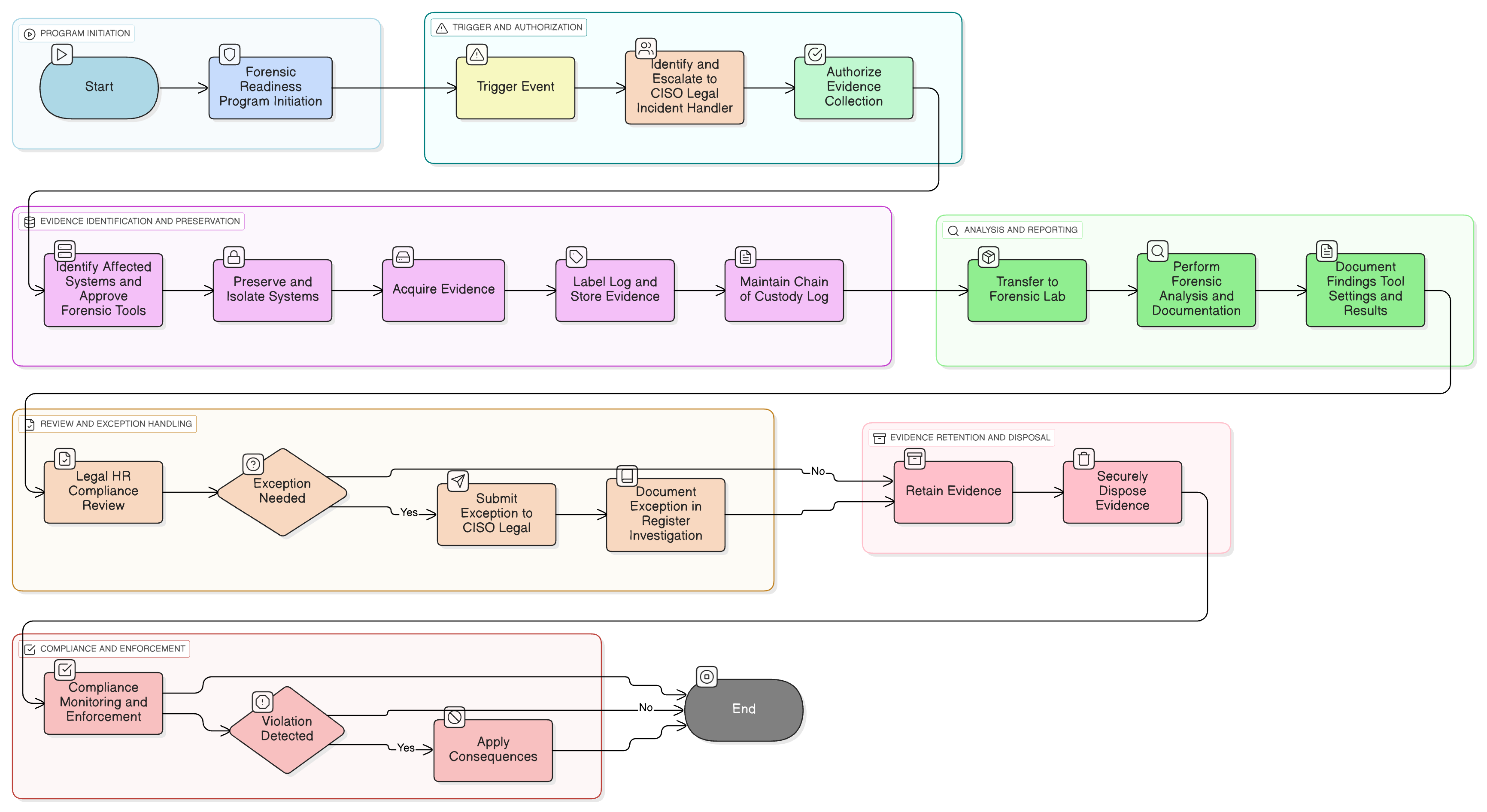
Click diagram to view full size
What's Inside
Scope and Rules for Evidence Collection
Forensic Readiness Program Requirements
Chain of Custody and Documentation
Toolset and Analysis Environment Controls
Regulatory and Data Protection Compliance
Exceptions, Enforcement, and Review Process
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| ISO/IEC 27035:2016 |
Part 1Part 3
|
| NIST SP 800-53 Rev.5 | |
| NIST SP 800-101 Rev.1 |
Mobile-Media Forensics
|
| NIST SP 800-86 |
Forensic Integration
|
| EU GDPR |
Article 5Article 33Article 34
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Audit Compliance Monitoring Policy
Validates adherence to forensic protocols and chain-of-custody requirements through regular audits.
Information Security Policy
Establishes the foundational mandate for investigation, evidence control, and compliance with applicable laws.
Change Management Policy
Ensures that systems under investigation are not altered during active forensic processes.
Data Retention And Disposal Policy
Governs the secure disposal and retention timelines for evidence and case-related data.
Cryptographic Controls Policy
Provides encryption requirements for storing and transferring sensitive or evidentiary data.
Logging And Monitoring Policy
Ensures availability of event logs and telemetry for evidence collection and forensic correlation.
Incident Response Policy
Defines incident triage and escalation pathways where forensic procedures are triggered.
About Clarysec Policies - Evidence Collection and Forensics Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Toolset Register & Validation
Maintains a validated register of forensic toolsets, supporting disk, memory, log, and timeline analysis for defensible investigations.
Immutable Evidence & Audit Trails
Requires unique labeling, integrity verification, and tamper-proof logs for every piece of digital evidence from acquisition to archive.
Exception & Risk Workflow
Provides structured approval, documentation, and mitigation procedures for evidence handling exceptions and risk scenarios.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
