Overview
This SME-focused Business Continuity and Disaster Recovery Policy provides a clear, compliant framework for maintaining operations and restoring critical IT services during disruptions, explicitly tailored for organizations without dedicated IT teams.
SME-Tailored Continuity
Designed for organizations without specialized IT teams, ensuring simplified yet effective business continuity and disaster recovery.
Clear Roles & Responsibilities
Defines actions for General Manager, IT providers, and staff for readiness, response, and recovery in any disruptive event.
Regulatory Compliance
Meets ISO/IEC 27001, GDPR, NIS2, DORA, and COBIT 2019 requirements for business continuity and operational resilience.
Tested & Audit-Ready
Mandates annual testing, documented lessons learned, and up-to-date plans for continuous improvement.
Read Full Overview
Policy Diagram
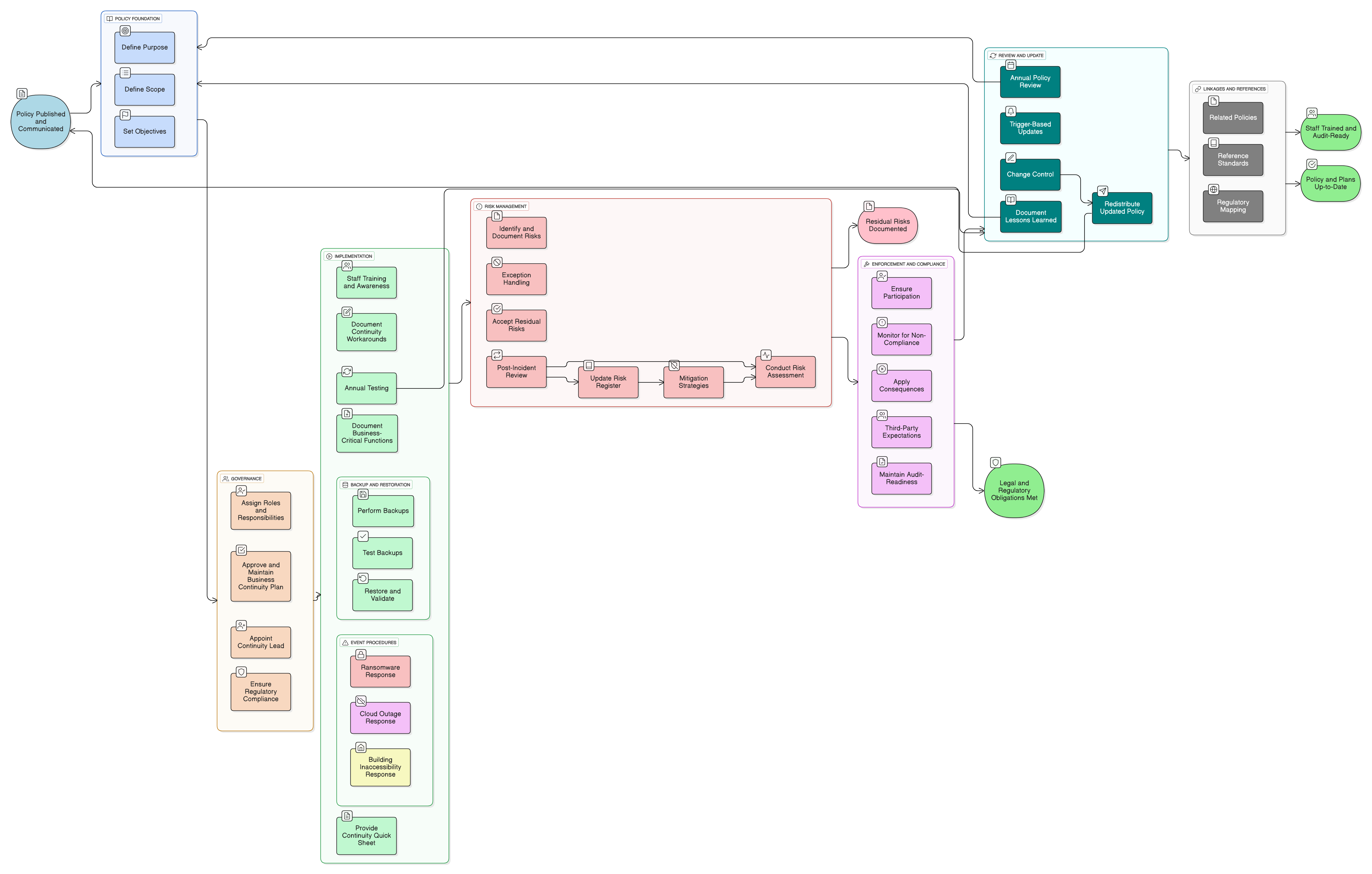
Click diagram to view full size
What's Inside
Scope and Roles for General Manager & IT Providers
Requirements for BCP, DR Playbooks, and Testing
Backup and Restoration Procedures
Risk Assessment and Residual Risk Acceptance
Legal & Regulatory Response Guidance
Audit-Readiness and Annual Review
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy-SME
Defines the high-level security objectives that continuity and recovery practices must support.
Access Control Policy-SME
Enables emergency revocation or restoration of user access during business disruption scenarios.
Risk Management Policy-SME
Forms the foundation for identifying, evaluating, and prioritizing continuity-related risks.
Information Security Awareness And Training Policy-SME
Ensures employees are prepared to act during disruptions and understand the BCP.
Backup And Restore Policy-SME
Provides specific technical procedures for safeguarding data availability and recovery.
Data Protection And Privacy Policy-SME
Ensures continuity planning respects personal data protections and complies with GDPR during and after incidents.
Logging And Monitoring Policy-SME
Supports detection of events that may trigger BC/DR processes, and provides forensic audit trails post-disruption.
Incident Response Policy-SME
Directly precedes activation of the recovery process in the event of cyber or operational incidents.
Evidence Collection And Forensics Policy-SME
Ensures digital evidence is captured during continuity scenarios for compliance, insurance, or investigation needs.
About Clarysec Policies - Business Continuity and Disaster Recovery Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Continuity Quick Sheet Provided
Key personnel get instant access to emergency procedures and contacts, printed and stored offsite for rapid use.
Scenario-Based Recovery Playbooks
Detailed, actionable steps for ransomware, cloud outages, and building inaccessibility minimize confusion during real incidents.
Risk Acceptance & Exception Handling
Residual risks are formally accepted, logged, and trigger reassessment, ensuring practical controls when mitigation isn’t possible.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
