Overview
This policy defines and governs how SMEs collect, handle, and store digital evidence during security incidents and investigations, ensuring integrity, legal compliance, and audit readiness with clear, practical roles for General Managers and IT providers.
Protect Evidence Integrity
Secure collection and storage procedures maintain chain of custody and prevent tampering or loss of digital evidence.
Clear SME Roles & Guidance
Empowers General Manager and IT providers with practical, defined responsibilities even without a full IT team.
Audit-Ready Processes
Simplified logging, documentation, and retention underpin legal, regulatory, and insurer requirements.
Forensic Readiness
Enables rapid evidence collection for incidents, internal decisions, or external investigations.
Read Full Overview
Policy Diagram
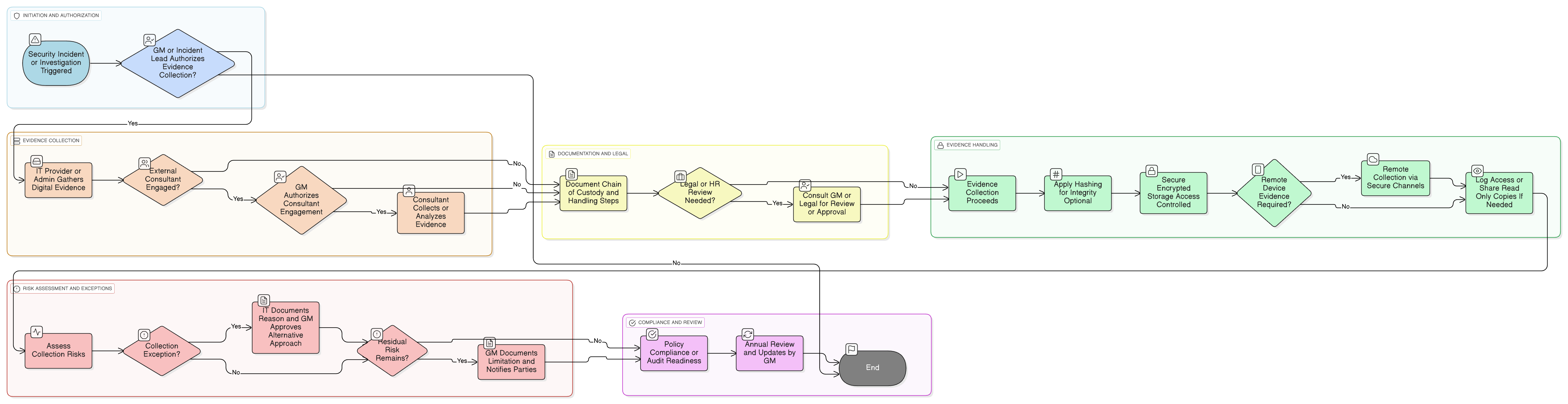
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles and Responsibilities for SMEs
Chain of Custody Documentation
Secure Evidence Storage Requirements
Risk Treatment and Legal Review
Audit Readiness Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Establishes authority over incident investigations, evidence decisions, and legal escalation.
Access Control Policy-SME
Ensures only authorized personnel can access sensitive systems and logs during investigations.
Logging And Monitoring Policy-SME
Provides the raw data used as forensic evidence and establishes retention, access control, and logging requirements.
Incident Response Policy-SME
Triggers the need for evidence collection and defines the operational flow leading to forensic preservation.
Data Protection And Privacy Policy-SME
Ensures any personal data collected as evidence is handled lawfully under GDPR and related regulations.
About Clarysec Policies - Evidence Collection and Forensics Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Simple Chain of Custody Tools
Provides Excel or template-based logs for tracking evidence, making thorough documentation practical for SMEs.
Remote Device Evidence Guidance
Details secure collection procedures for remote laptops and cloud data, supporting flexible, modern operations.
Policy-Driven Exception Handling
Specifies approval workflows and documentation for handling evidence when systems crash or media is corrupted.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
