Overview
This SME-adapted Risk Management Policy outlines roles, procedures, and governance for identifying, documenting, and treating business-wide risks, ensuring compliance with key standards.
Active Risk Management
Integrates ongoing risk identification and assessment into everyday business decisions for enhanced organizational resilience.
Simplified Roles for SMEs
Adapted for organizations without dedicated IT teams, leveraging the General Manager for top-level oversight.
Regulatory Alignment
Ensures compliance with ISO/IEC 27001:2022, NIST SP 800-53, EU NIS2, EU DORA, and COBIT 2019 standards.
Read Full Overview
Policy Diagram
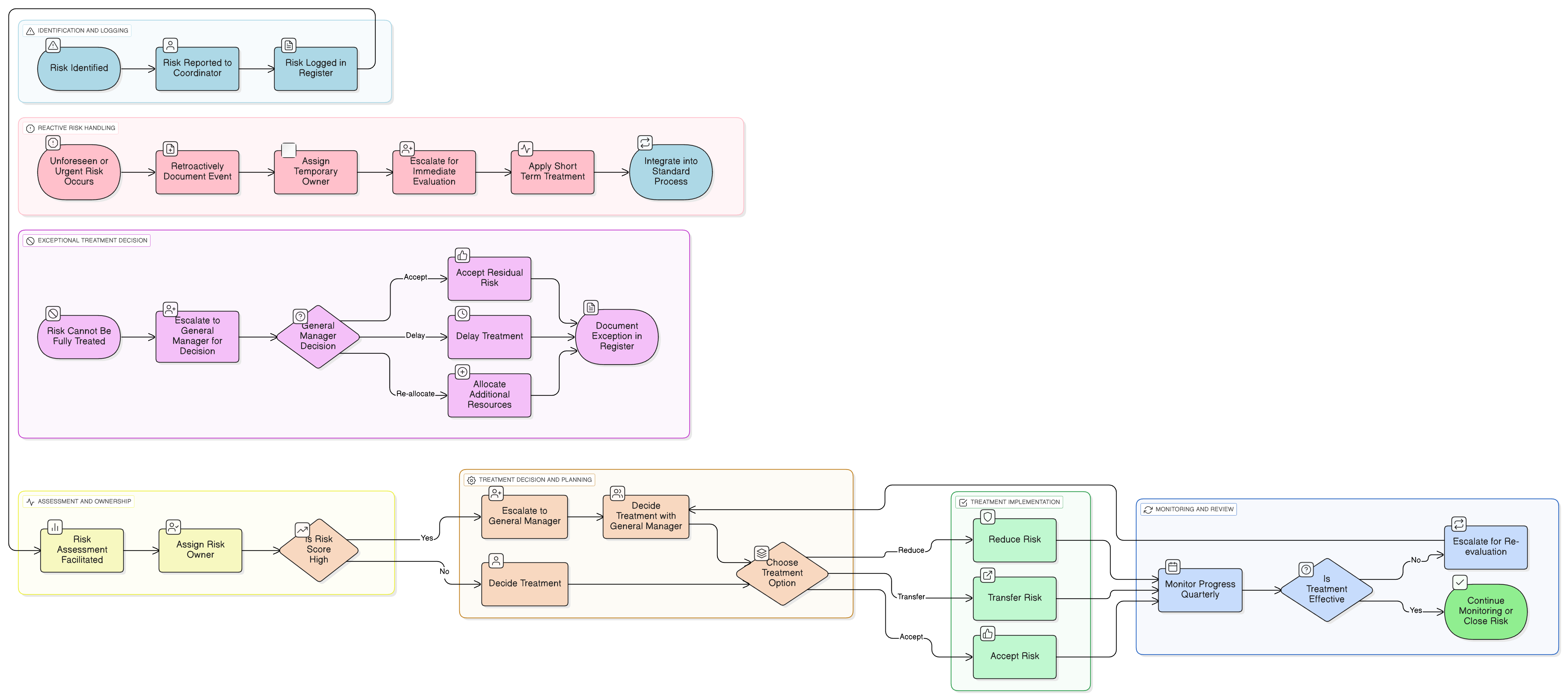
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Risk Register Management
Treatment and Exception Handling
Governance and Audit Requirements
KRIs and Monitoring
Policy Review and Communication
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Governance Roles And Responsibilities Policy-SME
Defines who is accountable for risk ownership and decision-making.
Business Continuity And Disaster Recovery Policy-SME
Identifies residual risks and recovery measures for critical services.
Change Management Policy SME
Requires risk assessment before implementing technical or process changes.
Data Protection And Privacy Policy SME
Addresses regulatory risk associated with handling of personal data.
Incident Response Policy SME
Ensures that risk treatment continues during and after security incidents.
About Clarysec Policies - Risk Management Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Ready-to-Audit Risk Register
Maintains a detailed, audit-ready risk register to simplify audits and demonstrate compliance at any time.
Clear Ownership Assignment
Designates specific owners for each risk and its treatment actions, preventing gaps and confusion across the SME.
Exception Management Built In
Documents, reviews, and escalates risk exceptions with clear approval steps and required follow-up dates.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
