Overview
This policy mandates the secure handling and management of test data and environments, ensuring data confidentiality, regulatory compliance, access controls, and operational integrity throughout all software testing activities.
Protect Sensitive Data
Enforces anonymization or masking of live data, preventing unauthorized use in test environments.
Segregated Environments
Requires logical and physical separation between test and production to prevent contamination.
Role-Based Access
Mandates RBAC, logging, and quarterly reviews to control and monitor access to test systems.
Read Full Overview
Policy Diagram
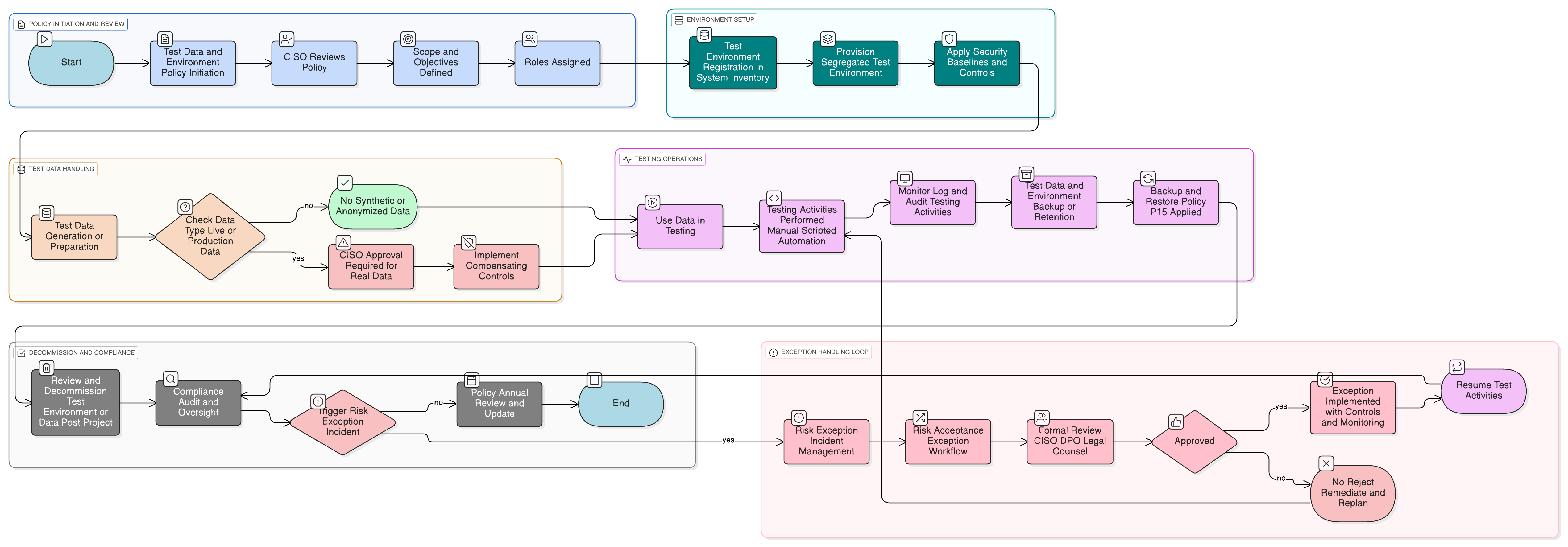
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Test Data Classification and Controls
Requirements for Secure Anonymization and Masking
Environment Segregation and Access Controls
Backup and Retention for Test Data
Monitoring, Exceptions, and Enforcement Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Audit Compliance Monitoring Policy
Enables validation of policy adherence and continuous assurance.
Information Security Policy
Establishes overarching security principles that govern test data protection and environment management.
Change Management Policy
Applies to creation, update, and decommissioning of test environments and deployment pipelines.
Data Classification And Labeling Policy
Guides test data selection and sensitivity-based control enforcement.
Data Retention And Disposal Policy
Defines retention timelines and secure disposal requirements for test datasets.
Backup And Restore Policy
Mandates backup practices and recovery validation for test environments.
Cryptographic Controls Policy
Specifies mandatory encryption standards for data at rest and in transit within test platforms.
Logging And Monitoring Policy
Governs visibility and anomaly detection for test environment activities.
Incident Response Policy
Defines escalation and remediation for breaches or incidents involving test systems.
About Clarysec Policies - Test Data and Test Environment Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Strong Vendor Controls
Enforces vendor risk assessment, NDAs, and explicit permissions for any third-party access to test data or environments.
Secure Toolchain Integration
Integrates controls into CI/CD pipelines, ensuring test builds cannot be mistakenly deployed into production.
Comprehensive Audit Trail
Requires full logging, incident review, and versioning for all test environment and data changes.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
