Overview
The Data Retention and Disposal Policy outlines organizational requirements for retaining and securely disposing of data, ensuring compliance with legal and regulatory frameworks, minimizing risk, and enforcing clear roles and governance across all data lifecycle stages.
Regulatory Compliance
Meets ISO/IEC 27001:2022, GDPR, NIS2, DORA, and COBIT 2019 retention and disposal requirements.
Secure Data Disposal
Enforces irreversible and documented destruction methods for digital and physical records.
Full Data Lifecycle Coverage
Covers creation, use, archival, and compliance-driven secure disposal for all data types.
Defined Roles & Responsibility
Assigns clear accountability to management, IT, data owners, third parties, and staff.
Read Full Overview
Policy Diagram
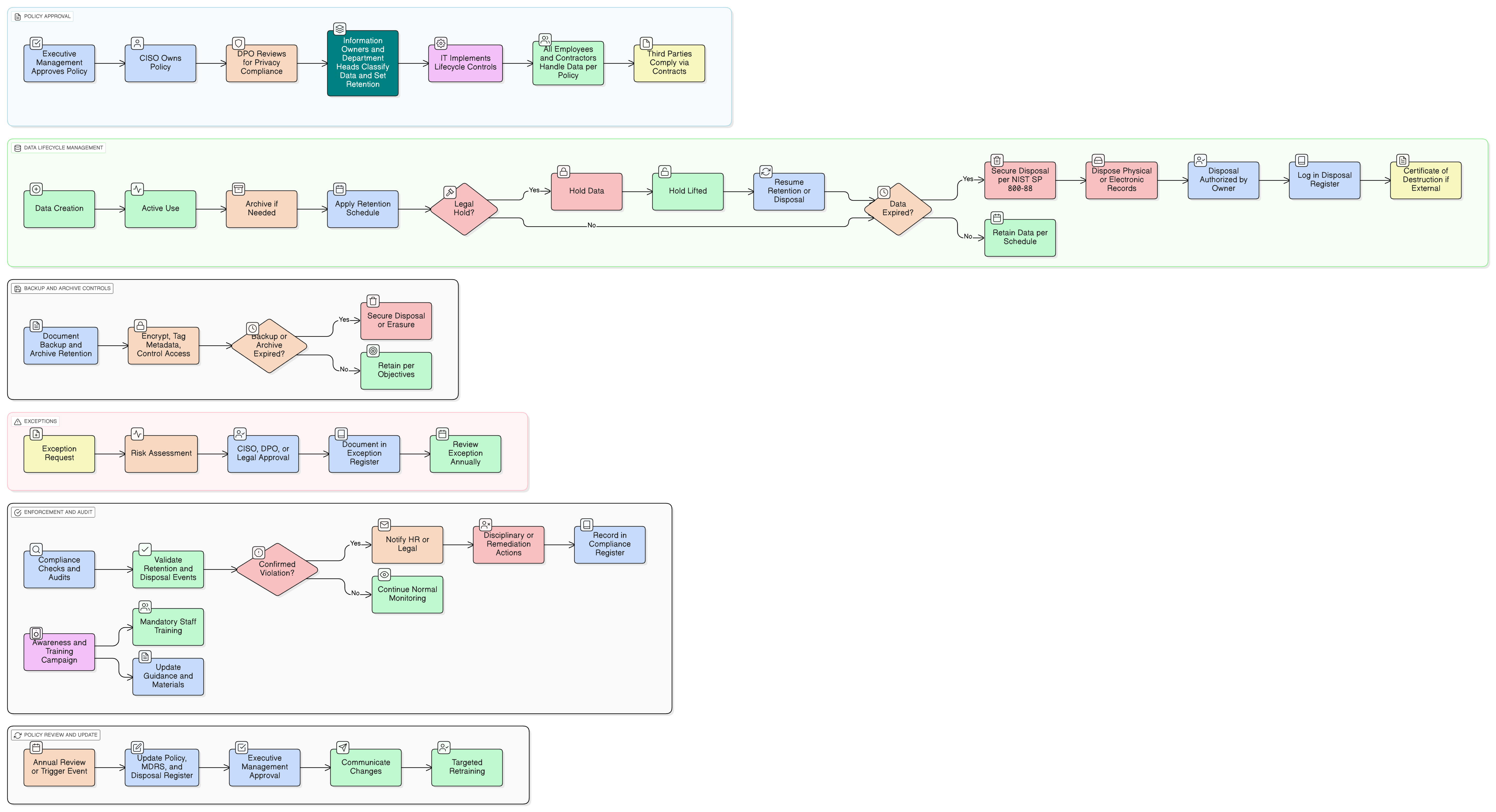
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Master Data Retention Schedule (MDRS) Governance
Retention & Disposal Processes for Digital and Physical Data
Legal Holds and Exception Management
Backup & Archive Data Handling
Third-Party and Vendor Disposal Controls
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Access Control Policy
Ensures that only authorized individuals access data during its retention period and that expired data is restricted pending disposal.
Asset Management Policy
Identifies which assets carry data requiring scheduled disposal and tracks their lifecycle from acquisition to destruction.
Data Classification And Labeling Policy
Guides classification decisions that directly influence how long data is retained and what disposal method is required.
Backup And Restore Policy
Defines retention periods and disposal procedures for backup media and replicated data assets.
Cryptographic Controls Policy
Supports cryptographic erasure for disposal and enforces encryption during data storage until destruction.
Incident Response Policy
Activated in cases where improper disposal results in potential data loss, breach, or regulatory violation.
About Clarysec Policies - Data Retention and Disposal Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Master Data Retention Schedule
Maps each information type to retention period, owner, legal basis, and disposal method for traceable, auditable policy compliance.
Automated Lifecycle Controls
Mandates system-driven tagging, scheduled purging, and alerts for effective lifecycle management and process integrity.
Exception and Legal Hold Guidance
Integrates documented exception process, legal hold protocols, and annual review for regulatory and operational flexibility.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
