Overview
This policy provides a structured approach to identify, assess, and manage risks related to dependency on critical suppliers, ensuring compliance with leading regulations and best practices while strengthening supply chain resilience.
Mitigates Single Points of Failure
Systematically identifies and reduces reliance on critical suppliers, minimizing operational disruptions.
Aligned with Latest Regulations
Ensures compliance with NIS2, DORA, ISO/IEC 27001:2022, and sector-specific supply chain laws.
Proactive Risk Monitoring
Implements continuous monitoring and annual reviews of supplier dependency risks and mitigations.
Contingency and Diversification Measures
Requires contingency plans and diversification strategies for all high-dependency suppliers.
Read Full Overview
Policy Diagram
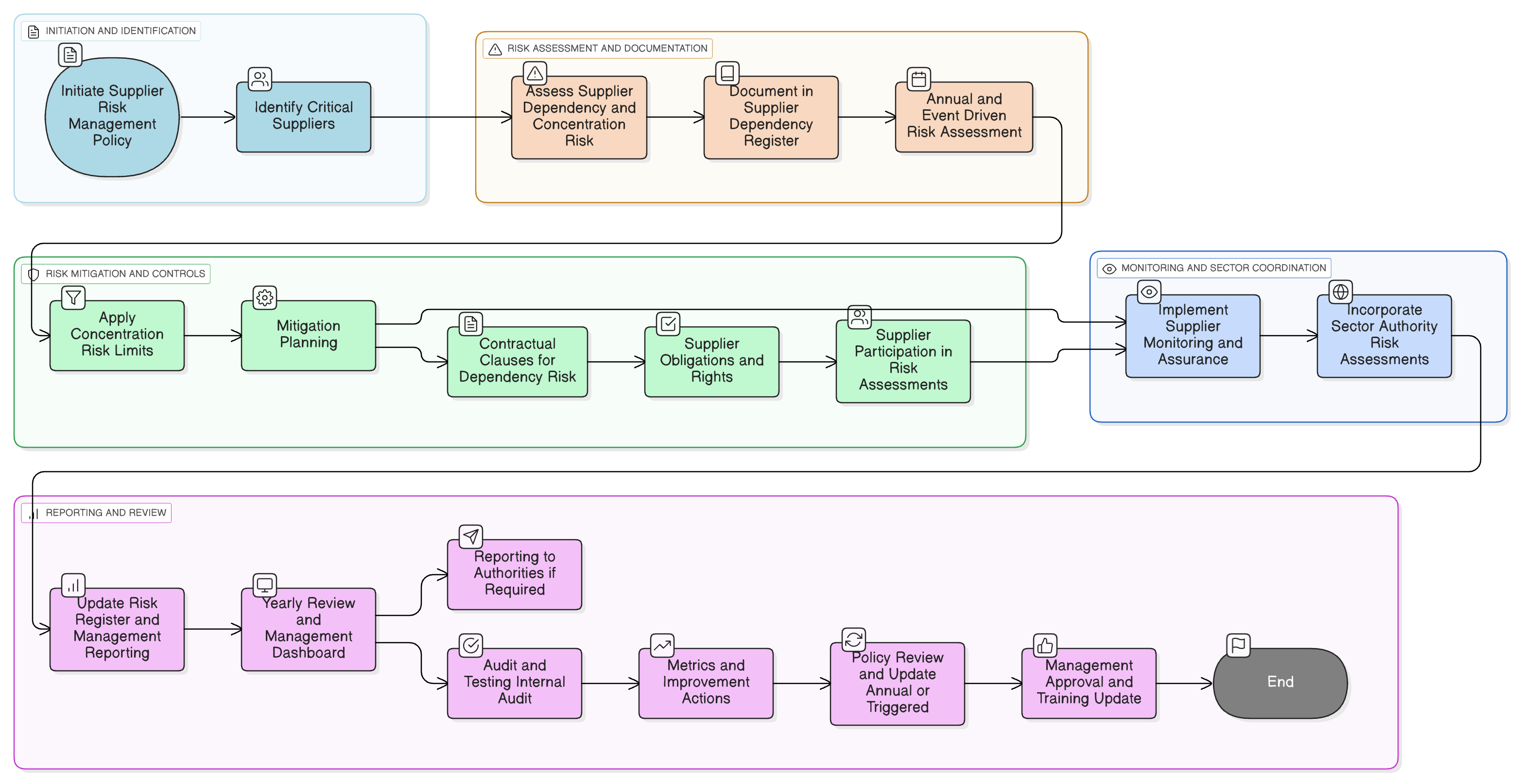
Click diagram to view full size
What's Inside
Supplier Dependency Register & Risk Criteria
Concentration Risk Limits & Mitigation
Sector-Specific Risk Incorporation (NIS2 Article 22)
Monitoring and Supplier Assurance
Annual Reviews and Audit Provisions
Contractual Clauses for Dependency Risk
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Art. 28Art. 32(1)(d)
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Governance Roles And Responsibilities Policy
Clarifies ownership for supplier risk decisions.
Information Security Policy
Assigns accountability for supplier dependency governance.
Risk Management Policy
Embeds concentration risk into enterprise risk registers.
Third Party And Supplier Security Policy
Baseline security; P41 adds dependency/concentration controls.
Cloud Usage Policy
Applies dependency criteria to cloud service adoption and exit plans.
Outsourced Development Policy
Covers dependency risks in external engineering.
Business Continuity And Disaster Recovery Policy
Plans for supplier outage/substitution scenarios.
Legal And Regulatory Compliance Policy
Ensures contracts/obligations reflect dependency controls.
About Clarysec Policies - Supplier Dependency Risk Management Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Role-Based Accountability
Assigns supplier risk tasks to specific enterprise functions, ensuring clear ownership and end-to-end process integrity.
Actionable Dependency Register
Maintains a detailed register of all critical suppliers, tracking dependencies, mitigations, and progress on risk reduction.
Integrated External Risk Intelligence
Rapidly incorporates sector-wide or authority-issued supply chain risk guidance into strategy and supplier controls.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
