Overview
The Outsourced Development Policy defines mandatory security, governance, and compliance controls for engaging third-party software developers, ensuring secure coding, proper vendor oversight, and risk-managed outsourced development throughout the organization.
End-to-End Vendor Security
Mandates due diligence, risk assessment, and secure coding for all third-party development partners.
Contractual Compliance
Requires legally binding security, IP ownership, and audit rights in every development agreement.
Comprehensive Access Control
Defines strict access, monitoring, and offboarding for external developers to safeguard code and systems.
Aligned with Major Standards
Supports ISO/IEC 27001, NIST, GDPR, NIS2, DORA, and COBIT 2019 compliance for third-party development.
Read Full Overview
Policy Diagram
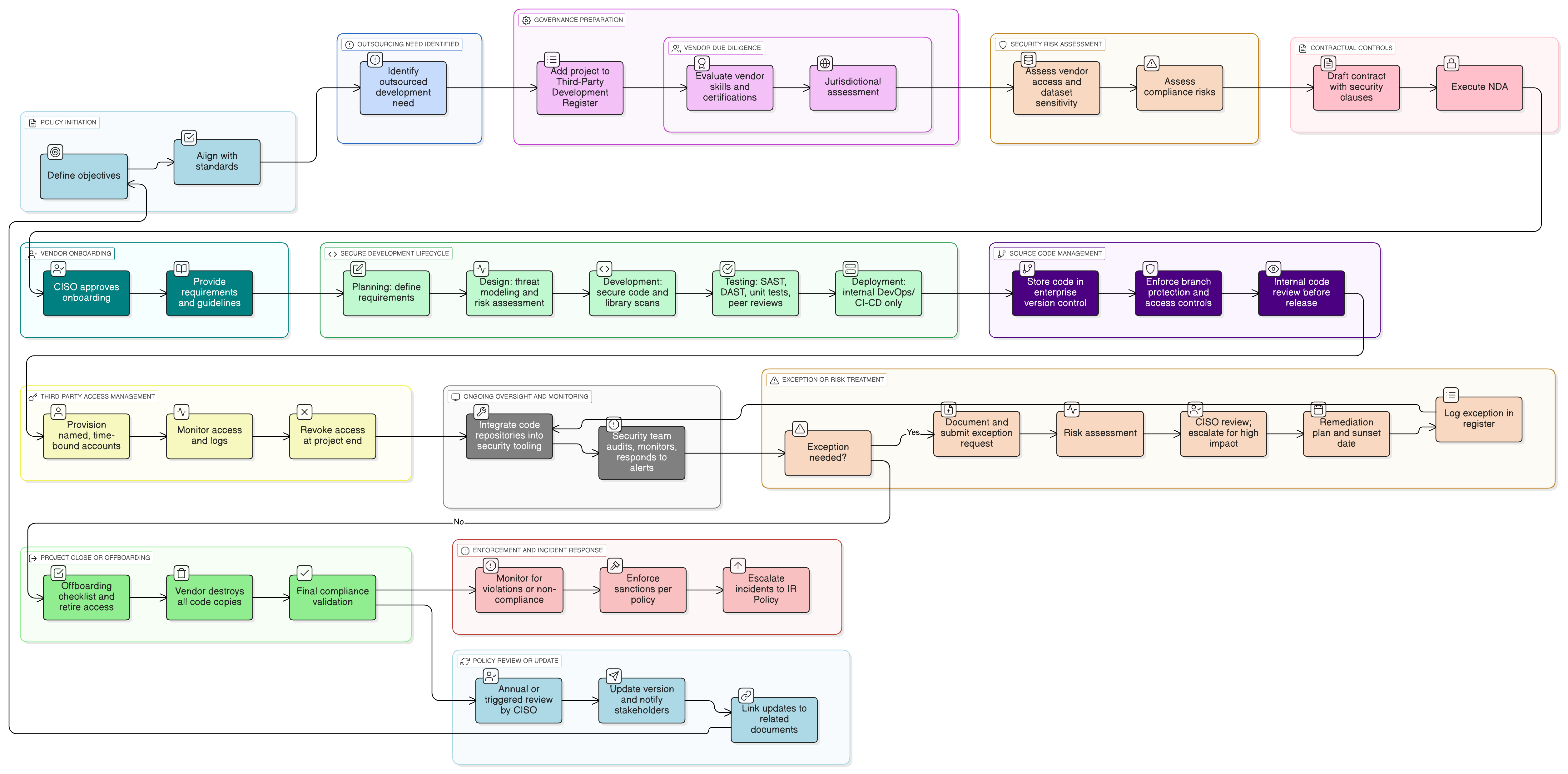
Click diagram to view full size
What's Inside
Scope and Rules for Outsourced Development
Third-Party Risk and Due Diligence Requirements
Mandatory Contractual Controls
Source Code Management Obligations
Exception and Risk Treatment Process
Compliance Monitoring and Enforcement
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Audit And Compliance Monitoring Policy
Provides requirements for reviewing outsourced development activities during audits or compliance reviews.
Information Security Policy
Establishes enterprise-level security principles that apply across internal and third-party development contexts.
Change Management Policy
Ensures all deployment-related changes from outsourced codebases are reviewed and approved prior to implementation.
Data Classification And Labeling Policy
Determines how sensitive data is identified before being exposed to development vendors or repositories.
Cryptographic Controls Policy
Guides how keys, secrets, and sensitive credentials must be handled during development and delivery.
Secure Development Policy
Defines baseline requirements for internal and external software development practices.
Incident Response Policy
Governs how breaches or security issues involving outsourced development are escalated, investigated, and resolved.
About Clarysec Policies - Outsourced Development Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Centralized Third-Party Register
Requires all outsourced development projects to be logged and tracked for audit, oversight, and compliance.
Defined Role-Based Accountability
Specifies clear responsibilities for management, CISO, procurement, and security teams in each engagement.
Integrated Monitoring & Tooling
Mandates security tool integration with vendor code, with automated compliance gates and active alert escalation.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
