Overview
This policy defines and enforces organizational governance models, assigning and documenting roles, responsibilities, and escalation processes for information security across the ISMS. It aligns with international standards and ensures accountability, cross-functional integration, and ongoing review of all governance activities.
Formal Role Assignment
Ensures responsibilities are clearly defined, assigned, documented, and regularly reviewed for robust security governance.
Integrated Cross-Departmental Oversight
Facilitates collaboration between executive, IT, risk, compliance, HR, and legal teams to enforce comprehensive security governance.
Escalation and Accountability
Enables transparent escalation paths and traceable decision-making for all operational, strategic, and compliance actions.
Read Full Overview
Policy Diagram
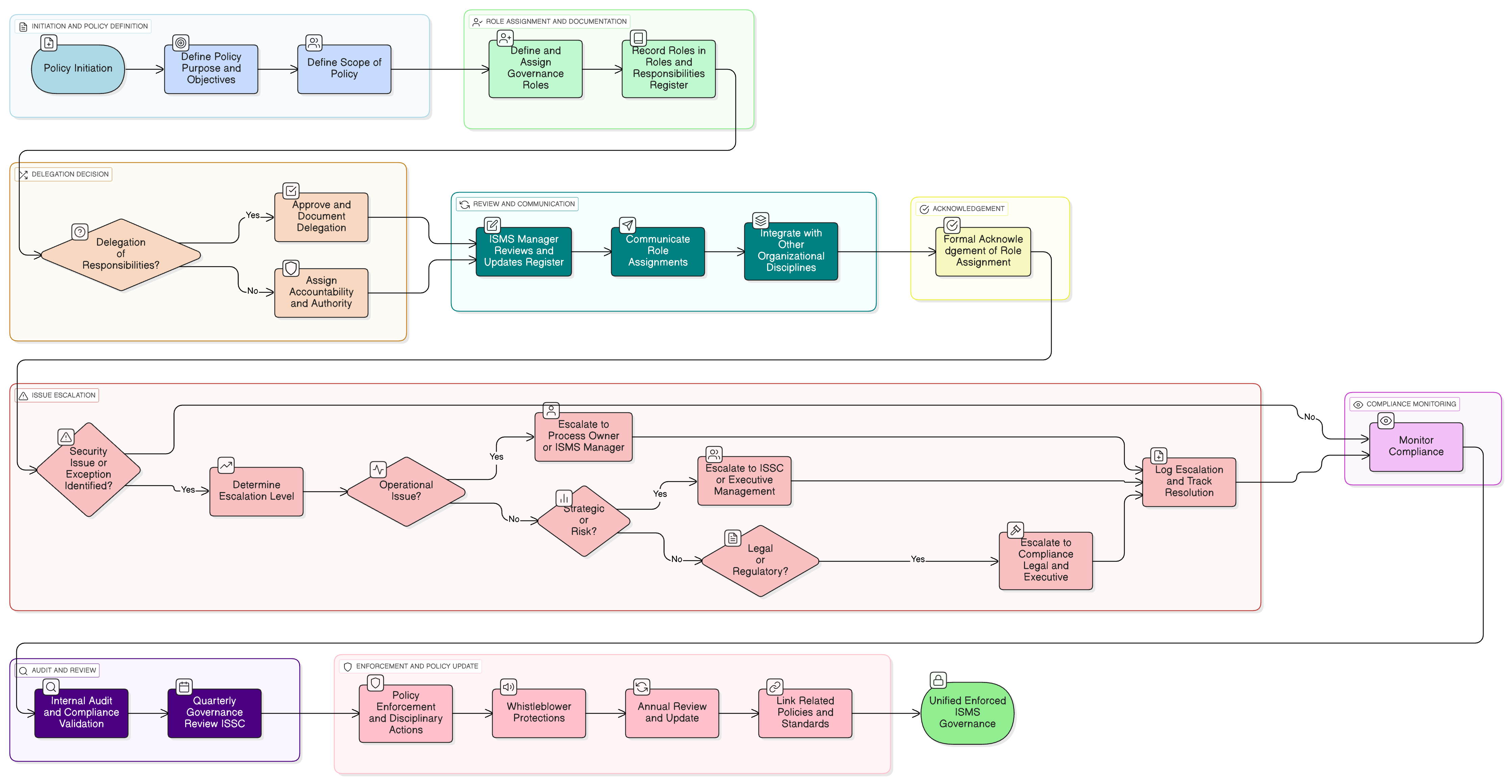
Click diagram to view full size
What's Inside
Governance Model and Structure
Roles & Responsibilities Register Requirements
Escalation Pathways and Procedures
Delegation and Accountability Rules
Integration with Risk and Compliance Frameworks
Periodic Review and Audit Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 5(1)(f)Article 24Article 37
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Audit Compliance Monitoring Policy
Supports independent review of governance effectiveness and enforces corrective actions for noncompliance.
Information Security Policy
Establishes the overall security program and outlines leadership responsibilities for policy endorsement and strategic oversight.
Change Management Policy
Ensures that changes to governance structures, roles, or responsibilities are subject to documented approval and risk review.
Risk Management Policy
Identifies and treats governance risks arising from role conflicts, unassigned duties, or lack of escalation.
Onboarding And Termination Policy
Enforces control assignment and revocation processes during personnel lifecycle changes.
About Clarysec Policies - Governance Roles and Responsibilities Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Multi-Tier Governance Structure
Implements layered oversight and decision-making, aligning security with operational, tactical, and strategic objectives.
Roles & Responsibilities Register
Maintains a centralized register of all security governance roles, delegations, authorities, and escalation pathways for traceable accountability.
Audit-Ready Compliance Tracking
Supports ongoing audit, review, and exception tracking, making governance gaps and corrective actions visible and manageable.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
