Overview
The Risk Management Policy (P06) establishes a unified, formal structure for identifying, analyzing, evaluating, and mitigating information security risks across all organizational units, in full alignment with ISO/IEC 27001, 27005, ISO 31000, and regulatory frameworks. It defines clear governance roles, centralizes risk registers and treatment plans, and enforces rigorous compliance, ensuring risks are proactively managed and escalated in accordance with the enterprise’s appetite and legal obligations.
Unified Risk Framework
Establishes consistent processes for identifying, analyzing, and treating information security risks organization-wide.
Regulatory Alignment
Mapped to ISO 27001, ISO 31000, NIST, GDPR, NIS2, and DORA for strong compliance and global best practices.
Centralized Risk Register
Maintains up-to-date, version-controlled register tracking risks, controls, owners, and mitigations.
Defined Roles & Accountability
Specifies governance, ownership, and escalation from asset owners to executive leadership for effective oversight.
Read Full Overview
Policy Diagram
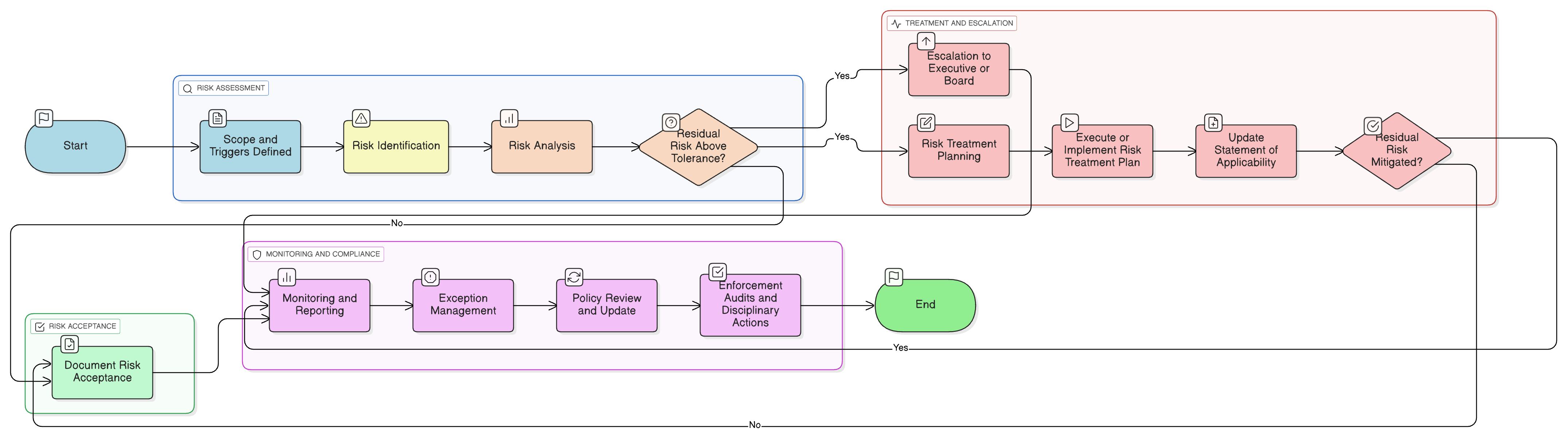
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Central Risk Register & Treatment Plan
Risk Assessment Methodology (ISO 27005, 31000, NIST 800-30)
Statement of Applicability (SoA) Updates
Exception and Escalation Procedures
Compliance, Review, and Audit Requirements
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27005:2024 |
Full risk lifecycle methodology
|
| ISO 31000:2018 |
Risk management principles and framework
|
| NIST SP 800-30 Rev.1 |
Risk Assessment Steps
|
| NIST SP 800-39 |
Organizational risk governance
|
| EU GDPR |
242532
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Governance Roles And Responsibilities Policy
Defines accountable owners and governance tiers referenced in the risk escalation matrix.
Audit Compliance Monitoring Policy
Validates policy adherence, including completeness of the Risk Register and evidence of treatments.
Information Security Policy
Sets the overall security governance model under which this risk policy operates.
Change Management Policy
Triggers risk reassessment for infrastructure and organizational changes.
Data Classification And Labeling Policy
Supports impact assessment during risk identification.
About Clarysec Policies - Risk Management Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Audit-Ready Traceability
Version-controlled register and SoA ensure every risk decision, control, and exception is fully traceable for audits and compliance reporting.
Proactive Escalation Matrix
Built-in KRI tracking and formal escalation thresholds enable fast response to emerging risks and executive sign-off when required.
Exception Lifecycle Control
Temporary deviations are risk-assessed, justified, scheduled for review, and must be approved, reducing unmanaged risks from process bypasses.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
