Overview
This policy provides strict, organization-wide standards for secure, compliant, and consistent handling of social media and all forms of external communications, minimizing reputational, legal, and regulatory risks.
Reduces Reputational Risk
Mitigate accidental leaks and unauthorized disclosures through strict communication governance.
Ensures Legal Compliance
Aligns communication with GDPR, NIS2, DORA, and more to avoid costly regulatory breaches.
Clarifies Roles & Responsibilities
Defines clear roles for Marketing, Legal, Security, and all personnel in external engagements.
Protects Sensitive Information
Prohibits sharing of confidential, financial, or client data via public channels.
Strengthens Brand Consistency
Enforces robust brand, content, and approval standards for all official statements.
Read Full Overview
Policy Diagram
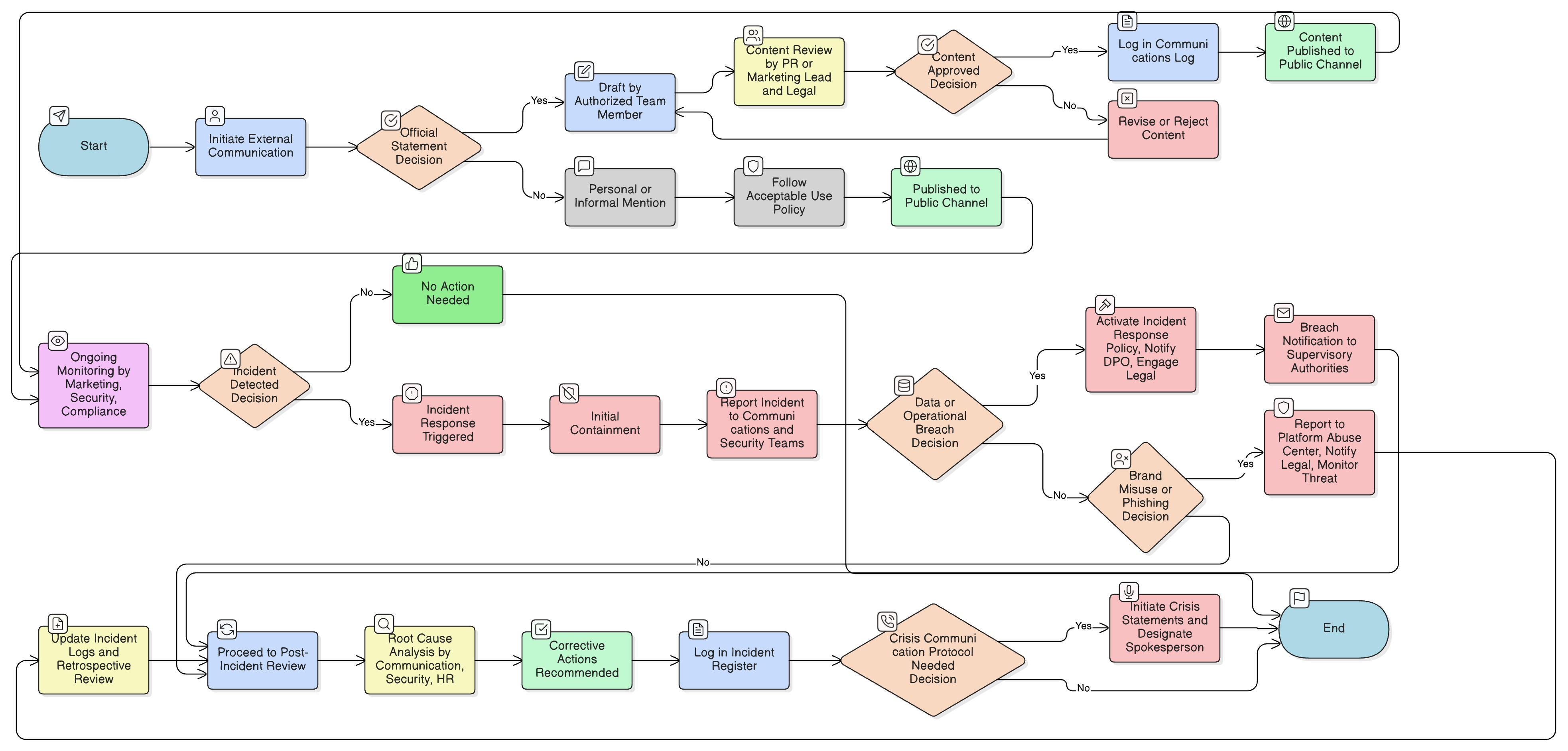
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles and Responsibilities
Account Security & Branding Requirements
Incident Response and Escalation
Policy Implementation Guidance
Compliance and Enforcement Standards
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Audit Compliance Monitoring Policy
Governs the audit processes that validate social media controls, monitoring systems, and compliance with external communication policies.
Information Security Policy
Establishes overarching principles for safeguarding information, which includes ensuring communications do not lead to unauthorized disclosure.
Acceptable Use Policy
Defines acceptable behaviors for digital platforms and technologies, which directly govern personal and professional use of social channels.
Risk Management Policy
Provides the risk framework for assessing threats related to public communication and reputational exposure.
Information Security Awareness And Training Policy
Mandates awareness programs that educate staff on secure communication practices and social engineering threats.
Data Classification And Labeling Policy
Guides personnel on what constitutes restricted or confidential information, which must not be disclosed externally.
Incident Response Policy
Defines how to handle public communication-related incidents, including data leaks, impersonation, and regulatory breach.
About Clarysec Policies - Social Media and External Communications Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Enforces Account Security Controls
Requires MFA, secure credential management, and continuous monitoring for all corporate social accounts.
Robust Incident Handling Protocols
Prescribes rapid containment, escalation, and post-incident reviews for communication breaches and threats.
Structured Exception Management
Allows documented, risk-assessed temporary exceptions for crisis or executive engagements with mandatory review.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
