Overview
This Acceptable Use Policy defines the rules for proper use of company IT resources, covering user behavior, prohibited actions, technical enforcement, reporting, and compliance in line with top security standards.
Comprehensive User Controls
Covers all user types and devices to minimize misuse, negligence, and abuse of corporate IT resources.
Risk-Based Enforcement
Combines technical safeguards with clear user obligations to reduce behavior-based security risks.
Integrated Awareness & Training
Mandates policy acknowledgment and regular training to reinforce secure, ethical system use.
Legal & Regulatory Alignment
Meets requirements from ISO/IEC 27001, GDPR, NIS2, and more for audit-ready compliance.
Read Full Overview
Policy Diagram
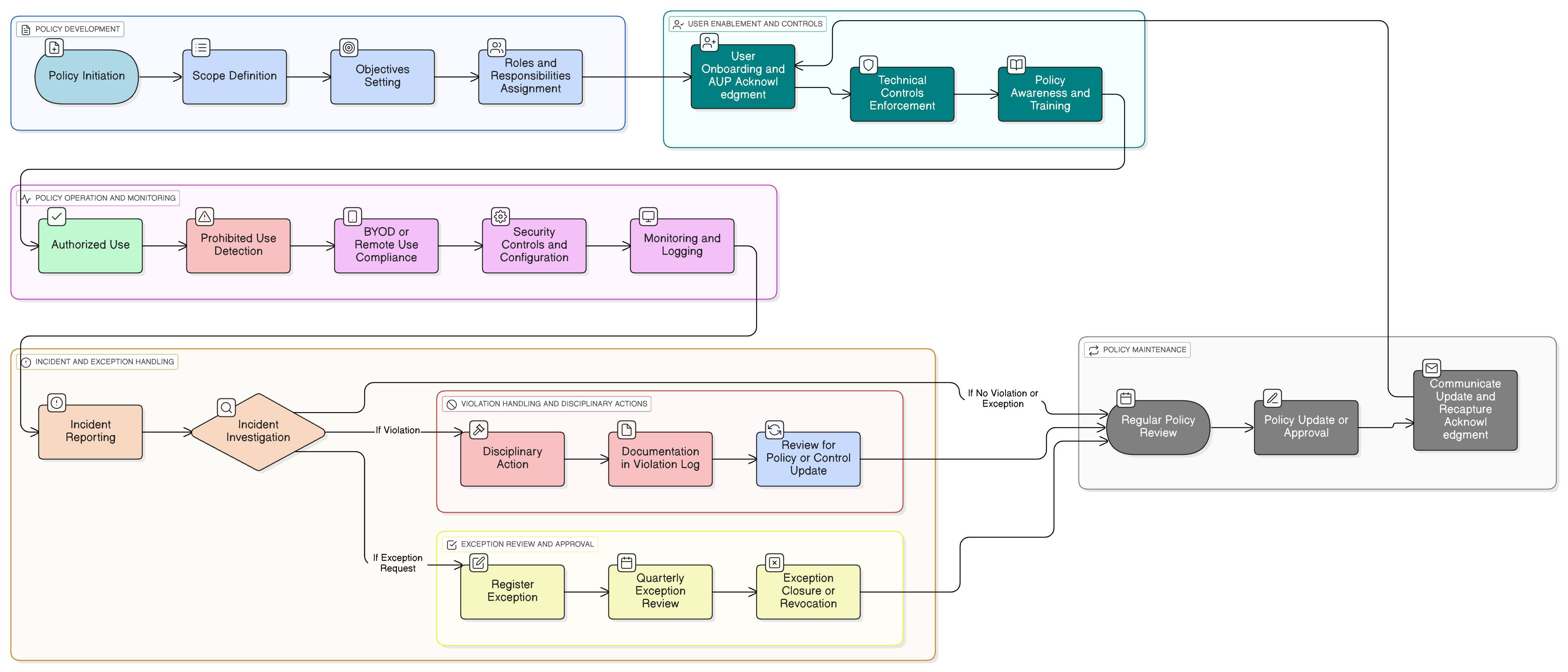
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
User Behavior and Access Rules
Prohibited Activities List
BYOD and Remote Use Requirements
Incident Response and Reporting
Policy Exception and Disciplinary Process
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 5(1)(f)Article 32Recital 39
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Information Security Policy
Establishes the foundational behavior expectations and senior leadership commitment to acceptable use.
Access Control Policy
Defines permissions and rights associated with users, systems, and data access, directly enforcing acceptable use boundaries.
Risk Management Policy
Addresses behavior-related risks and supports monitoring and treatment activities associated with user-driven threats.
Onboarding And Termination Policy
Ensures acceptable use terms are acknowledged at entry and revoked at departure.
Remote Work Policy
Extends acceptable use provisions to remote and hybrid work environments.
About Clarysec Policies - Acceptable Use Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Multilayer Role Accountability
Assigns enforcement, escalation, and compliance review to distinct teams: management, IT, HR, legal, and end users.
Exception Built-In Workflow
Defines granular exception handling steps with approval, controls, audit, and periodic review for safe non-standard use.
Automated Monitoring & Response
Enables real-time policy violation detection, logging, and incident initiation for swift containment and evidence gathering.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
