Overview
This policy mandates structured, risk-based security awareness and training programs for all users with system or data access, ensuring ongoing compliance and reduced security risks.
Comprehensive Coverage
Applies to employees, third parties, contractors, and anyone with access to organizational information.
Role-Based & Risk-Informed
Tailors security training to job roles, specific risk exposures, and regulatory needs.
Continuous Reinforcement
Ensures periodic refresher, real-time, and ad hoc training, with performance-tracked campaigns.
Read Full Overview
Policy Diagram
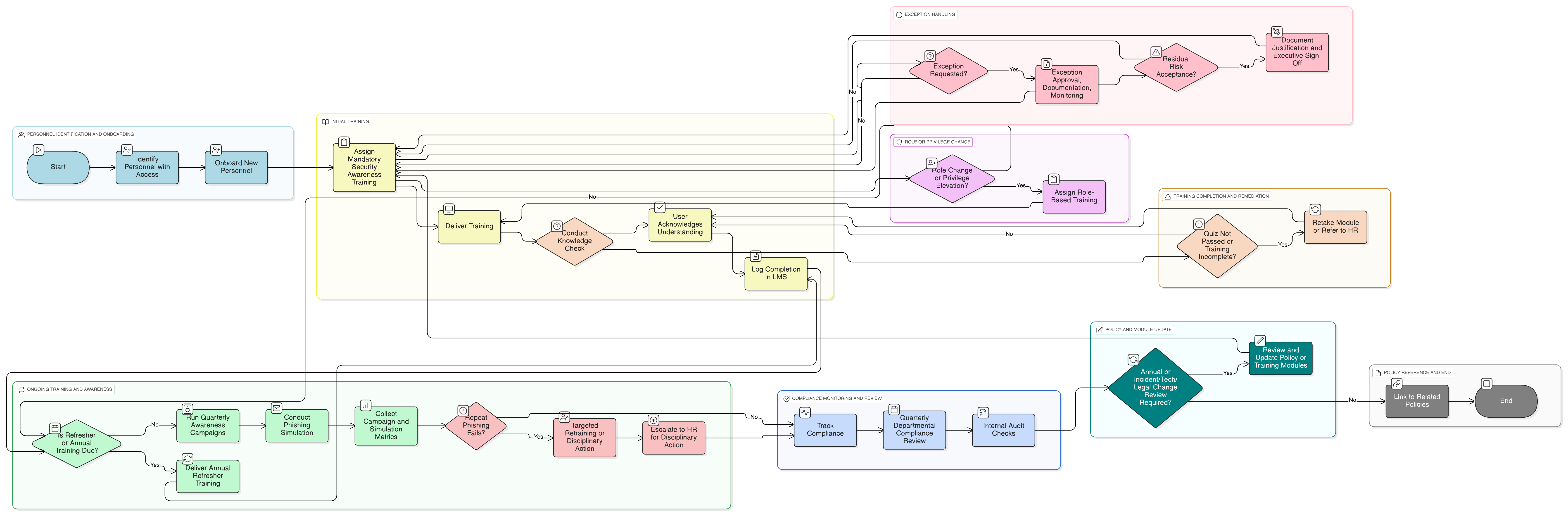
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Role-Specific Training Process
Periodic and Ad Hoc Awareness Campaigns
Simulated Phishing & Social Engineering Exercises
Tracking, Recordkeeping & Policy Acknowledgment
Exception & Enforcement Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 32Article 39Recital 78
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Audit Compliance Monitoring Policy
Validates that awareness controls are operational, measurable, and effective during audits.
Information Security Policy
Establishes security awareness as a foundational control in the organization’s ISMS.
Acceptable Use Policy
Requires user acknowledgment during training and clarifies responsibilities tied to daily technology use.
Onboarding And Termination Policy
Ensures training is embedded at entry and tracked throughout employment.
Risk Management Policy
Links human-centric training to threat modeling and residual risk reduction strategies.
About Clarysec Policies - Information Security Awareness and Training Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Automated Tracking & Enforcement
Integrates automated training reminders, escalation paths, and compliance dashboards for timely completion and HR action.
Live Metrics & Behavioral Analytics
Uses phishing simulation results and user feedback to benchmark and refine training effectiveness across departments.
Accessible & Localized Content
Training materials are designed for accessibility, cultural relevance, and are offered in multiple formats for diverse teams.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
