Overview
The Security Testing and Red-Teaming Policy provides a structured approach for regular vulnerability and penetration testing, as well as red team exercises. It aims to uncover and remediate weaknesses in critical systems, ensure compliance with NIS2 and other regulations, and support continuous improvement through reporting, training, and periodic review.
Structured Security Testing
Defines regular vulnerability assessments, penetration tests, and red team exercises for all critical information systems.
NIS2 and Regulatory Alignment
Meets NIS2 Article 21(2)(f) and EU regulations by formalizing continuous cybersecurity effectiveness evaluations.
Comprehensive Governance
Details authorization, reporting, and remediation processes ensuring accountability and compliance.
Continuous Improvement Focus
Incorporates lessons learned from tests into risk management and incident response for ongoing security enhancement.
Read Full Overview
Policy Diagram
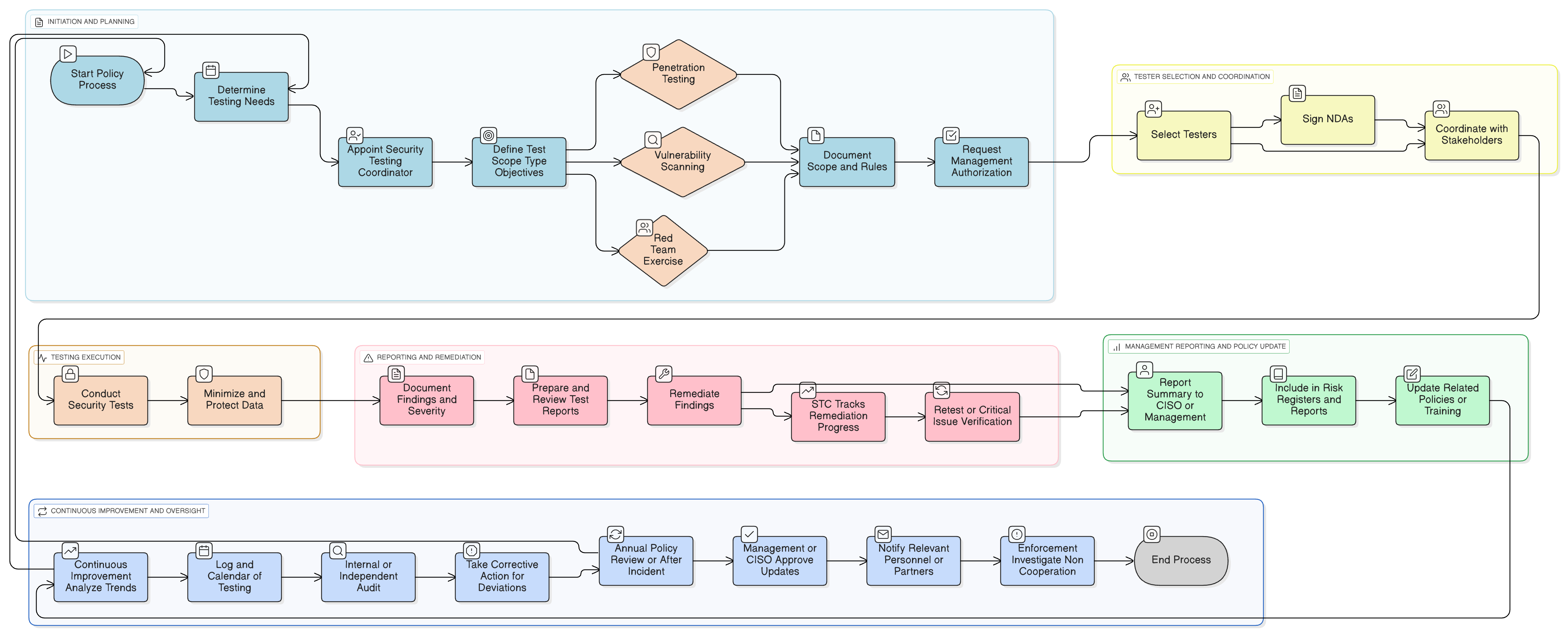
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Testing Methodology (Vulnerability, PT, RT)
Authorization and Reporting Procedures
Remediation and Verification Requirements
Training and Awareness Measures
Third-Party and Supplier Testing
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Audit And Compliance Monitoring Policy
Independent oversight of testing program effectiveness.
Risk Management Policy
Testing outputs drive risk evaluation and treatment.
Logging And Monitoring Policy
Validates detection coverage during exercises.
Secure Development Policy
Integrates test findings into SDLC controls.
Application Security Requirements Policy
Ensures requirements reflect test learnings.
Incident Response Policy
Red-team scenarios refine playbooks and response.
Evidence Collection And Forensics Policy
Collects artifacts during testing safely.
Business Continuity And Disaster Recovery Policy
Exercises verify resilience under attack.
About Clarysec Policies - Security Testing and Red-Teaming Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Defined Roles and Accountability
Assigns clear responsibilities to STC, security teams, and system owners for planning, authorization, and remediation of security tests.
Robust Documentation and Audit Trail
Mandates detailed logs, test reports, and reviews, simplifying audits and regulatory proof of testing activities and outcomes.
Controlled Physical and Social Engineering Tests
Safely incorporates facility and personnel security evaluations, coordinated with HR and physical security for minimal disruption.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
