Overview
The Secure Communications and Multi-Factor Authentication Policy defines mandatory requirements for using MFA and encrypted communication channels across the organization to protect sensitive information, enhance access controls, and comply with NIS2, ISO/IEC, and other regulatory standards, while ensuring secure emergency systems and ongoing user awareness.
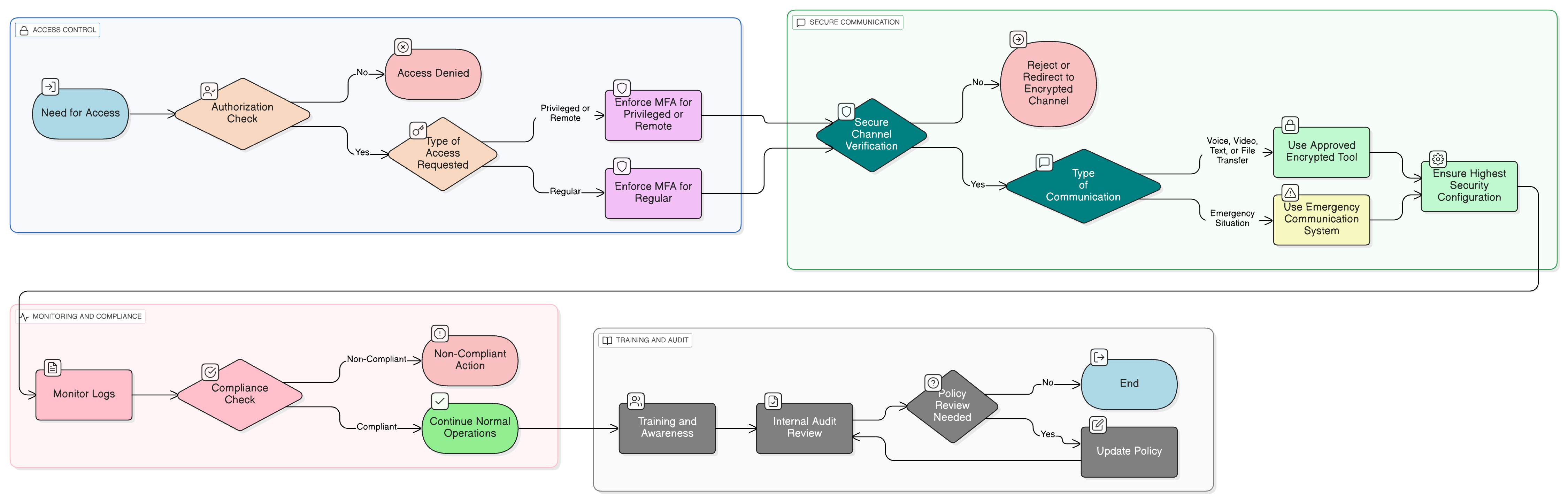
Enforces Secure Communication
Mandates encryption and approved secure channels for voice, video, and messaging, protecting sensitive information from interception.
Mandatory Multi-Factor Authentication
Requires MFA for all access to systems, including privileged and remote users, to significantly reduce risk of unauthorized entry.
Emergency Communication Safeguards
Secures emergency systems and mandates periodic testing to ensure crisis communications remain protected and available.
Comprehensive User Training
Provides regular training on secure channel use, MFA best practices, and identification of insecure options for all users.
Read Full Overview
Policy Diagram
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
MFA Implementation Requirements
Secure Communication Channel Controls
Privileged Account Security
Emergency Communication Safeguards
User Awareness and Training Requirements
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy
Mandates enterprise-wide authentication and communications safeguards.
Access Control Policy
Establishes access governance that MFA in P38 enforces.
User Account And Privilege Management Policy
Ties MFA to privileged access lifecycle.
Cryptographic Controls Policy
Provides approved crypto/key management for secure comms.
Network Security Policy
Secures transport channels used by voice/video/messaging.
Logging And Monitoring Policy
Monitors authentication events and secure-channel usage.
Business Continuity And Disaster Recovery Policy
Secures emergency communications during crises.
Information Security Awareness And Training Policy
Trains users on MFA and channel hygiene.
About Clarysec Policies - Secure Communications and Multi-Factor Authentication Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Tightly Integrated Regulatory Alignment
Meets NIS2, GDPR, DORA, and ISO/IEC standards for authentication and communication security, closing compliance gaps for enterprises.
Defined Accountability for Every Role
Assigns explicit responsibilities to CISO, IT, and response coordinators, ensuring clear, enforceable security processes.
Gap-Filling Emergency Channel Controls
Extends controls to emergency comms, requiring periodic drills and secure access, bridging a traditional policy weakness.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
