Overview
The Access Control Policy defines mandatory principles and controls for restricting and managing access to systems, facilities, and data based on business roles and regulatory demands. It establishes processes for granting, reviewing, and revoking access, ensuring that only authorized users have permissions aligned to their responsibilities and job needs.
Strong Role-Based Controls
Implements least privilege, need-to-know, and segregation of duties to safeguard systems and data.
Integrated Identity Lifecycle
Coordinates access provisioning, revocation, and updates with HR and technical workflows.
Regulatory Alignment
Built to meet ISO/IEC 27001, NIST SP 800-53, GDPR, NIS2, DORA, and COBIT standards.
Automated Access Reviews
Requires evidence-based, quarterly reviews for user rights and privileged access.
Comprehensive Scope
Applies to all users, systems, and hybrid environments including BYOD and third parties.
Read Full Overview
Policy Diagram
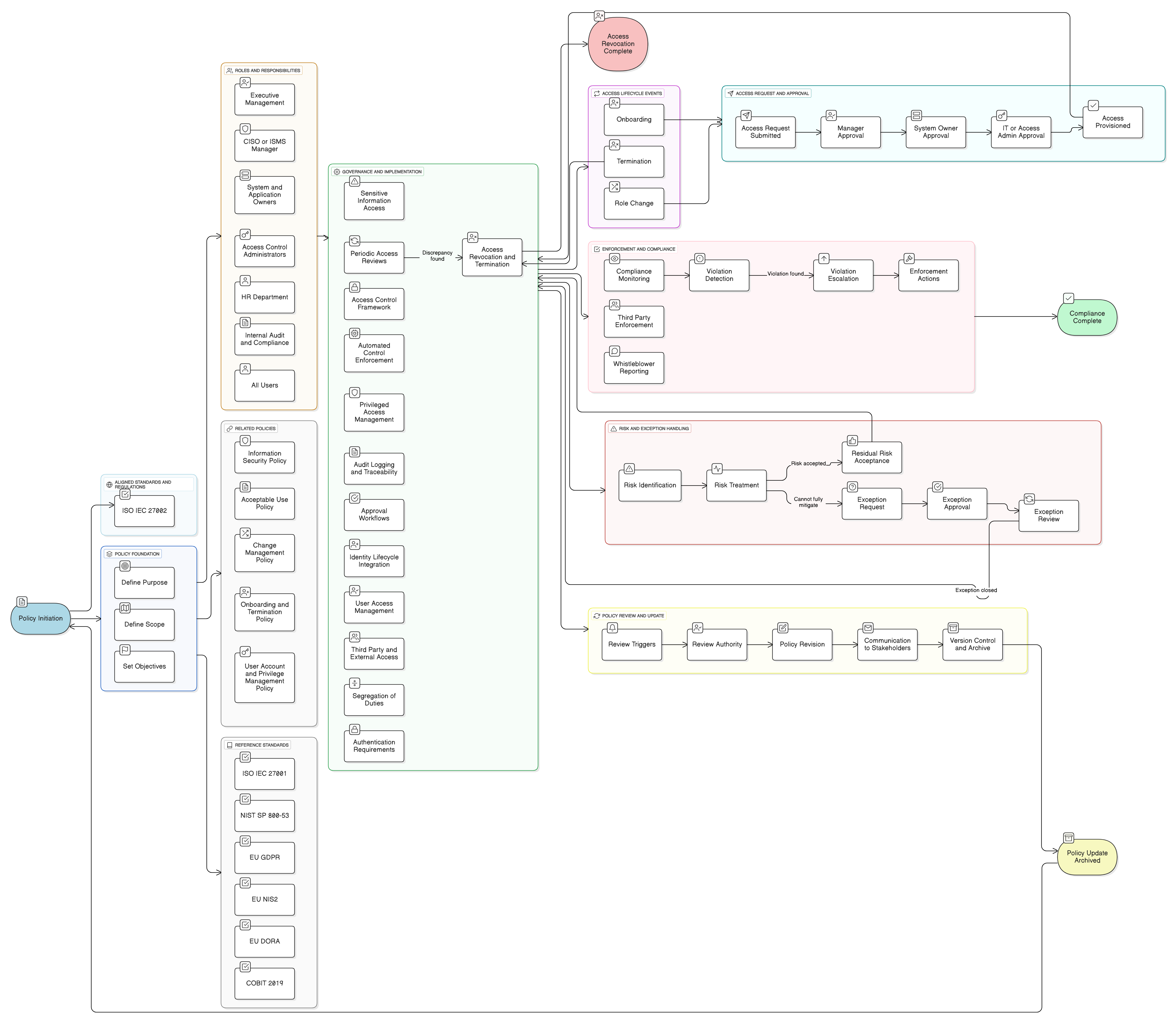
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Approval and Revocation Workflows
Privileged Access Management
Identity Lifecycle Integration
Third-Party and Supplier Testing
Periodic Access Reviews
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
5(1)(f)32(1)(b)Recital 39
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Information Security Policy
Defines the organization’s security commitment and high-level access control expectations.
Acceptable Use Policy
Sets behavioral conditions for access and user accountability for responsible system usage.
Change Management Policy
Governs how changes to access configurations, roles, or group structures must be implemented and tested securely.
Onboarding And Termination Policy
Drives the initiation and revocation of access rights in accordance with user lifecycle events.
User Account And Privilege Management Policy
Operationalizes account-level controls and complements this policy with technical access enforcement guidelines.
About Clarysec Policies - Access Control Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Automated Enforcement & Alerts
Integrates automated provisioning and alerts for failed deprovisioning, orphaned accounts, and access violations.
Detailed Exception Tracking
Requires justification, approval, and periodic review for all access control exceptions, minimizing uncontrolled risks.
Seamless Third-Party Security
Mandates contractually enforced, time-bound, and monitored access for external vendors and partners.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
