Overview
This Network Security Policy defines the mandatory controls and governance required to protect organizational networks from unauthorized access, data leakage, and service disruption. It mandates segmentation, firewall enforcement, monitored remote access, and ongoing compliance with leading cybersecurity regulations and best practices.
Layered Network Protection
Implements segmentation, firewall enforcement, secure routing, and centralized network monitoring for maximum defense.
Clear Roles & Governance
Defines responsibilities for IT, security, and operations in protecting, monitoring, and auditing network infrastructure.
Aligned with Global Standards
Ensures compliance with ISO/IEC 27001:2022, GDPR, NIS2, DORA, COBIT, and more for regulatory assurance.
Read Full Overview
Policy Diagram
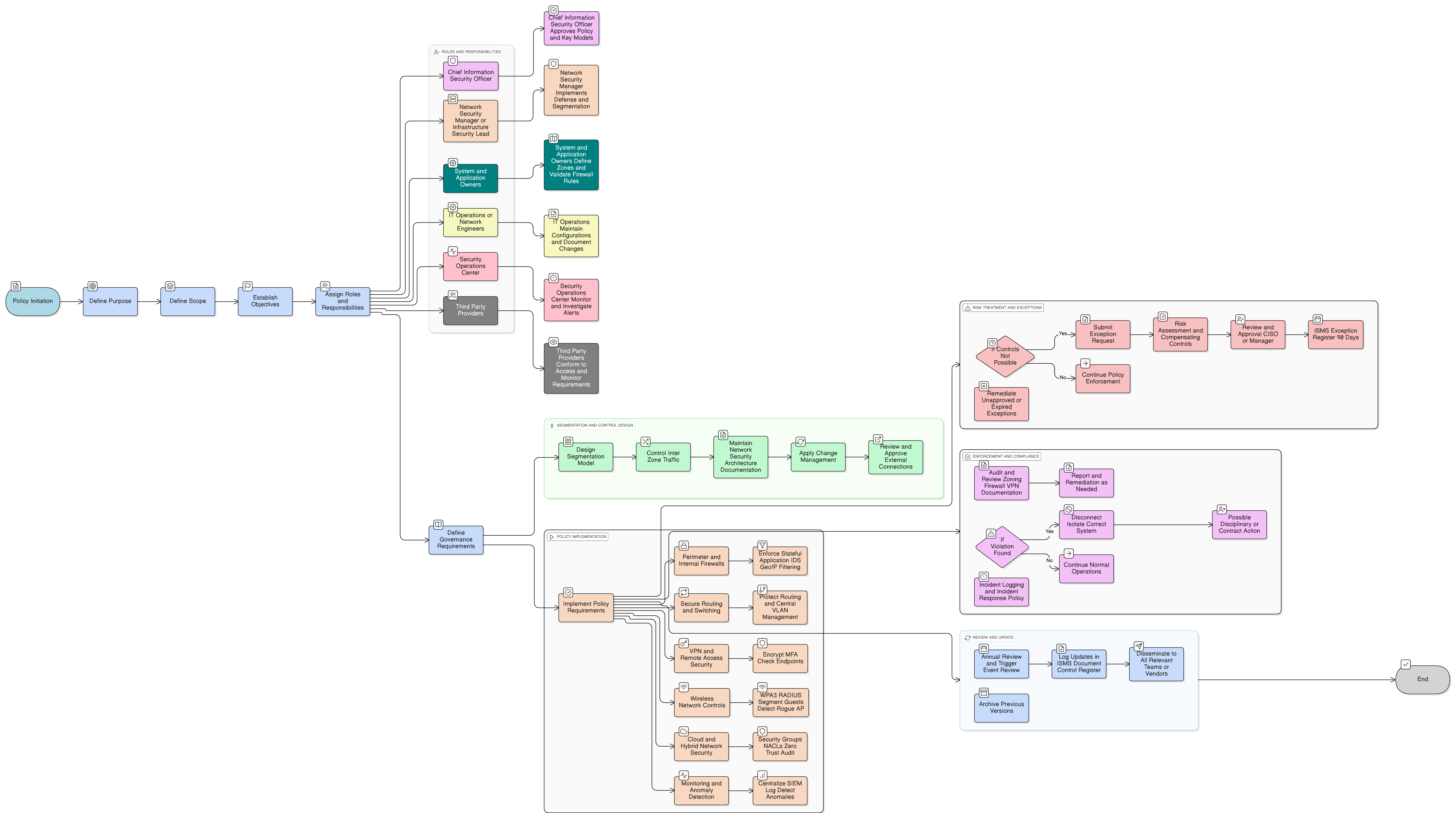
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Segmentation and Firewall Requirements
Cloud, VPN, and Wireless Controls
Roles and Responsibilities
Exception Handling and Review
Monitoring and Logging Mandates
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 32
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Information Security Policy
Establishes foundational security principles and mandates layered protections, including network-based access and threat controls.
Access Control Policy
Ensures that network segmentation is enforced in alignment with user roles, least privilege principles, and access provisioning rules.
Change Management Policy
Regulates firewall modifications, VPN rule adjustments, and routing changes through a documented and auditable process.
Asset Management Policy
Supports the identification and classification of networked systems and ensures all connected assets are managed under policy-defined scopes.
Logging And Monitoring Policy
Governs the collection, correlation, and retention of network logs including firewall events, access attempts, and anomaly detections.
Incident Response Policy
Defines the escalation, containment, and eradication procedures in response to network-borne threats or intrusions, such as DDoS, lateral movement, or unauthorized access.
About Clarysec Policies - Network Security Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Rigorous Change Control & Exception Handling
Mandates formal change management and exception reviews, reducing unapproved changes and enabling rapid, auditable mitigation.
Automatic Audit Trails & Traceability
Requires logging, review, and secure archiving for all updates and exceptions, ensuring traceability and regulatory response.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
