Overview
This policy mandates structured, auditable controls for user account and privilege management across all organizational systems, ensuring access is authorized, monitored, and compliant with major security standards.
Enforced Least Privilege
Access rights and privileges are assigned strictly on a need-to-know basis, minimizing the risk of unauthorized access.
Comprehensive Scope
Applies to all user accounts, including staff, contractors, and vendors, across cloud, on-premises, and remote environments.
Robust Authentication
Mandates strong authentication with password complexity, multi-factor authentication, and controls on privileged sessions.
Read Full Overview
Policy Diagram
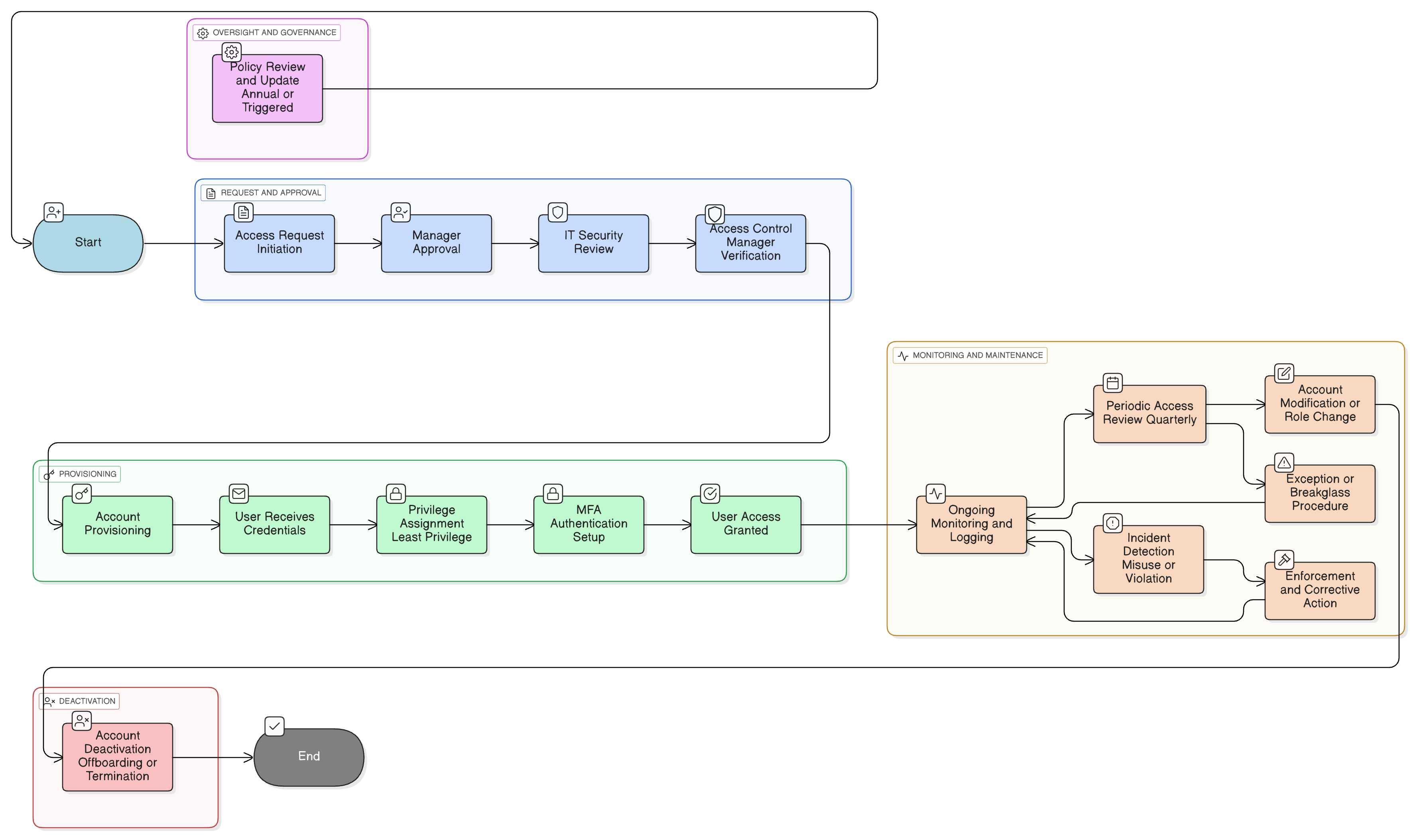
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Privilege Assignment and Management
Authentication and Session Controls
Third-Party and Vendor Access Procedures
Periodic Access Reviews
Exception and Risk Treatment Processes
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Access Control Policy
Establishes the overarching access control principles and mechanisms, including rule-based and role-based controls.
Onboarding And Termination Policy
Provides procedural steps for initiating and terminating user access aligned with HR actions.
Information Security Awareness And Training Policy
Reinforces user responsibilities for account security and credential safeguarding.
Data Classification And Labeling Policy
Guides access levels based on data classification, ensuring privilege boundaries align with sensitivity tiers.
Logging And Monitoring Policy
Ensures audit trails are collected for all account-related activities and reviewed to detect anomalies or unauthorized usage.
Incident Response Policy
Governs escalation, containment, and post-incident actions in cases of privilege misuse or unauthorized account activity.
About Clarysec Policies - User Account and Privilege Management Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Clear Accountability by Role
Specifies granular responsibilities for CISO, IT admin, HR, managers, and vendors, clarifying approval and audit chains.
Automated Onboarding & Offboarding
Requires IAM integration with HRMS for timely, automated provisioning and deactivation of user accounts.
Trackable Exception Management
Formal, risk-based process for exceptions, ensuring all deviations are documented, approved, and auditable.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
