Overview
This policy defines mandatory requirements for securing and managing mobile devices and BYOD access to organizational data, ensuring compliance and risk mitigation for all users.
Comprehensive Security Controls
Ensures encryption, authentication, and isolation of corporate data on all mobile and BYOD devices.
Regulatory Compliance
Aligns with ISO/IEC 27001, GDPR, NIS2, DORA, and NIST standards for mobile data protection.
Enforced Device Management
Requires MDM enrollment, patching, and whitelisted applications to reduce risk and support monitoring.
Role-Based Access & Accountability
Clearly defines responsibilities for users, managers, IT/security, HR, and legal for mobile device usage.
Read Full Overview
Policy Diagram
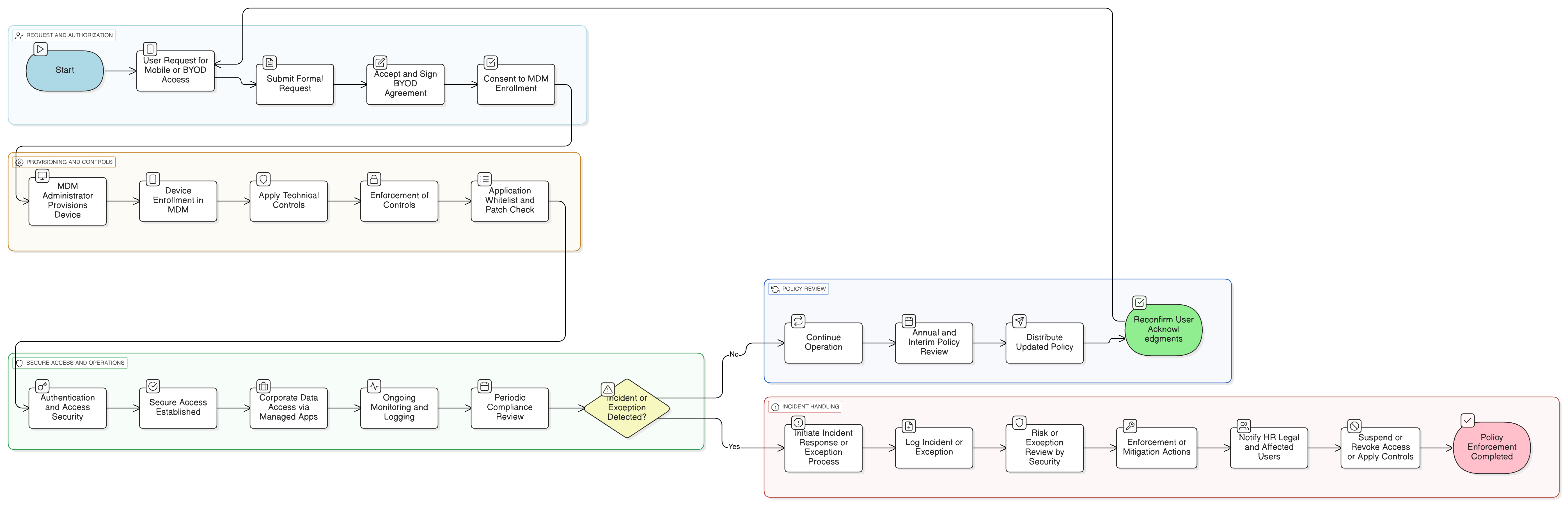
Click diagram to view full size
What's Inside
Scope and Applicability for Devices & Users
MDM Enrollment and Security Requirements
Authentication and MFA Controls
BYOD Process and User Consent
DLP, Containerization, and Data Isolation
Exception and Risk Mitigation Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Audit Compliance Monitoring Policy
Provides the basis for periodic checks on mobile security compliance, including BYOD policy adherence.
Information Security Policy
Establishes the overarching governance principles for all information security controls, including those governing mobile device usage.
Acceptable Use Policy
Defines permissible behaviors and restrictions related to technology usage, which directly apply to mobile and BYOD access.
Remote Work Policy
Addresses additional security obligations for mobile work environments, complementing mobile-specific controls defined in this policy.
Data Classification And Labeling Policy
Governs how data on mobile devices must be handled based on classification level, impacting storage, transfer, and encryption enforcement.
Logging And Monitoring Policy
Supports the collection and review of mobile access logs to detect anomalies or violations.
Incident Response Policy
Governs how mobile-related incidents (e.g., device loss, unauthorized access) are handled and escalated.
About Clarysec Policies - Mobile Device and BYOD Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Privacy Safeguards for BYOD
Integrates privacy rights by separating personal and corporate data, ensuring user consent and transparency in monitoring.
Rapid Risk & Exception Handling
Allows controlled exceptions with enforced risk mitigation and rapid access suspension during investigations or compliance events.
Automated Compliance Action
Non-compliant devices are automatically quarantined or revoked, reducing manual intervention and remediation delays.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
