Overview
The Clear Desk and Screen Policy defines strict requirements and controls for securing sensitive information in all physical and hybrid work environments, ensuring regulatory compliance and organizational discipline.
Mandatory Workspace Security
Enforces secure handling of documents, screens, and devices to prevent unauthorized access or data loss.
Regulatory Compliance
Supports ISO/IEC 27001, GDPR, NIS2, COBIT, and more with verifiable clean desk and screen controls.
Applies to All Personnel
Covers employees, visitors, contractors, and remote workers across all physical and hybrid environments.
Technical and Physical Controls
Mandates screen locks, secure storage, and regular policy validation for robust defense against breaches.
Read Full Overview
Policy Diagram
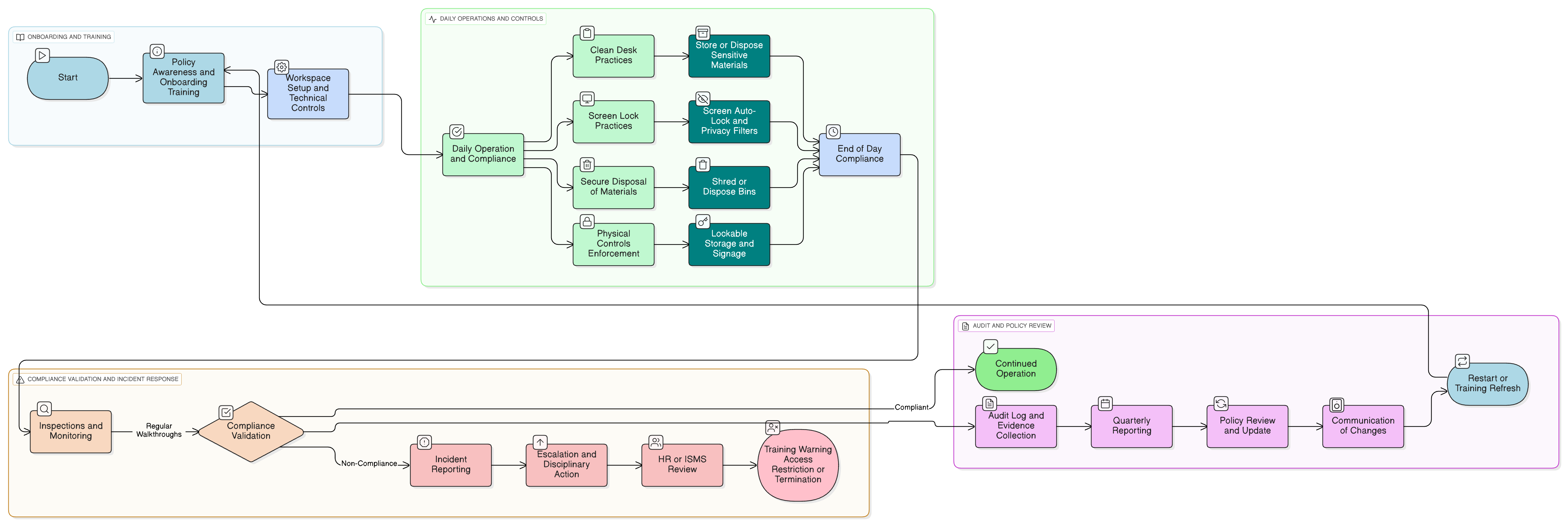
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles & Responsibilities
Physical & Technical Workspace Controls
Clear Screen Requirements
Remote Work and Third-Party Handling
Audit, Enforcement & Exception Management
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy
Establishes user behavior and physical security expectations foundational to this policy.
Acceptable Use Policy
Addresses user accountability for protecting data and systems, including physical environments.
Risk Management Policy
Incorporates physical workspace risks as part of enterprise-wide information risk analysis.
Asset Management Policy
Supports tracking and secure handling of devices and media left at desks.
Data Classification And Labeling Policy
Links to clean desk enforcement for physical documents labeled Confidential or Internal.
Data Retention And Disposal Policy
Guides physical document retention, shredding, and bin-handling practices.
Logging And Monitoring Policy
May be used to monitor workstation lock status, idle time, or workspace camera feeds where allowed.
About Clarysec Policies - Clear Desk and Clear Screen Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Role-Based Accountability
Defines clear responsibility for executives, managers, IT, Facilities, and all personnel, driving compliance and effective enforcement.
Hybrid & Remote Ready
Extends requirements and verification to home offices, hot-desking, and shared workspaces, ensuring secure data anywhere.
Inspection & Audit Trail
Regular walkthroughs and infraction tracking enable real-time validation, ensuring readiness for internal and external audits.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
