Overview
The Time Synchronization Policy mandates consistent, accurate time configuration across all IT and cloud systems to support secure logging, regulatory compliance, and reliable incident response.
Centralized Time Accuracy
Mandates trusted NTP sources and drift detection for audit compliant, reliable logs and transactions.
Supports Regulatory Compliance
Aligns with ISO 27001, GDPR, DORA, NIS2, and more for audit traceability and secure operations.
Automated Drift Detection
Enforces scheduled synchronization, anomaly alerts, and escalation if clock drift thresholds are exceeded.
Applies to All Stakeholders
Covers employees, contractors, and vendors managing on-prem or cloud-based, time-sensitive systems.
Read Full Overview
Policy Diagram
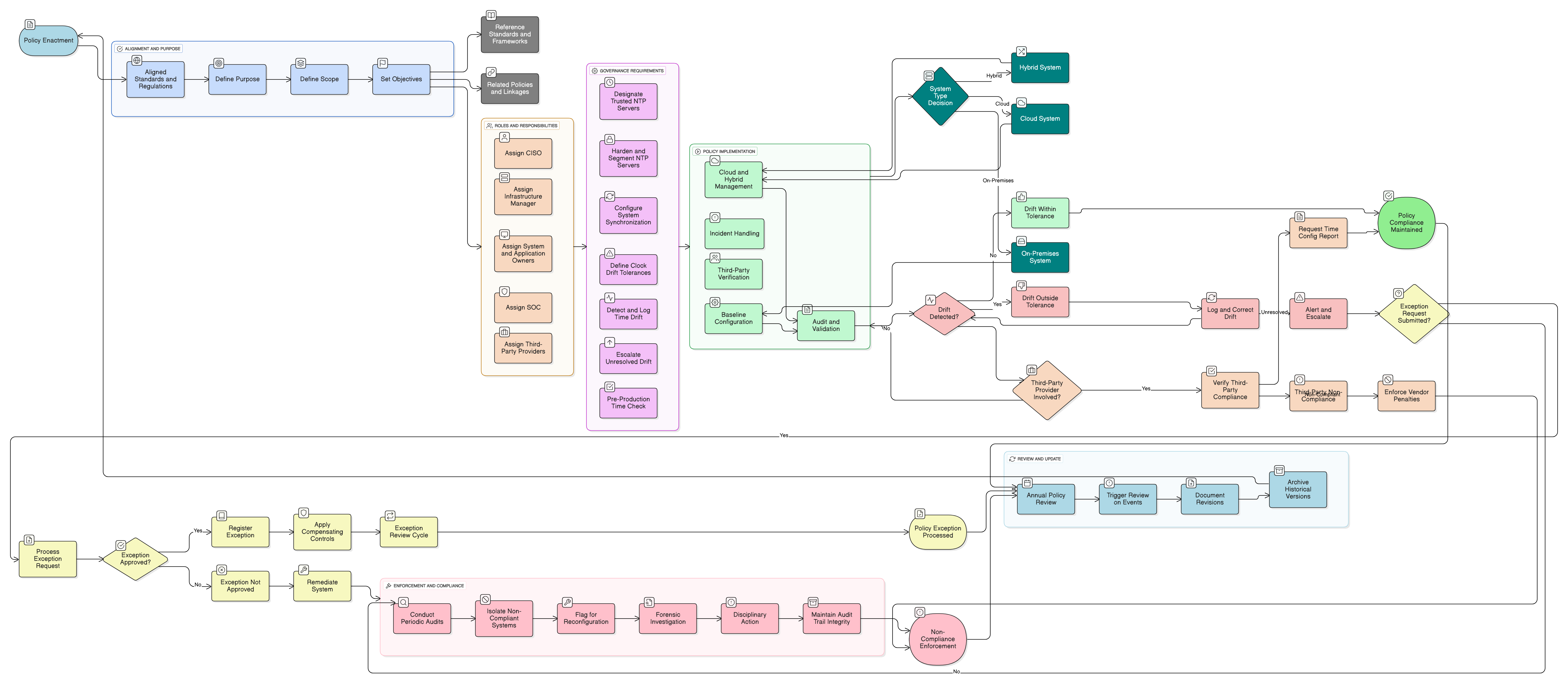
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles and Responsibilities
Governance and Exception Handling
Drift Detection & Escalation
Audit and Validation Mechanisms
Policy Enforcement & Compliance
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 32
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Endpoint Protection And Malware Policy
Requires time-accurate alerting and behavioral analysis to detect malware spread, lateral movement, and access anomalies.
Information Security Policy
Establishes the overarching mandate to ensure the integrity and traceability of all information systems, for which time accuracy is foundational.
Change Management Policy
Governs modifications to system configurations including time source adjustments, ensuring proper documentation, testing, and rollback plans.
Logging And Monitoring Policy
Directly dependent on synchronized time to ensure event sequencing, log correlation, and incident investigation integrity across diverse systems.
Incident Response Policy
Relies on accurate timestamps for forensic investigations, incident timelines, and chain-of-custody evidence. Inaccurate time undermines credibility of incident reports.
Risk Management Policy
Defines the treatment of desynchronization as a potential operational and forensic risk, requiring controls defined in this policy to mitigate impact.
About Clarysec Policies - Time Synchronization Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Structured Exception Management
Formal process for risk-based time sync exceptions, including remediation and required review cycles.
Forensic-Grade Audit Trail Integrity
Isolation and marking of logs during time anomalies ensure chain-of-custody and regulatory defensibility.
Cross-Cloud Consistency
Mandates unified time configuration for hybrid, cloud, and on-prem systems, reducing replay and log mismatch risks.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
