Overview
This Endpoint Protection / Malware Policy details mandatory measures to prevent, detect, contain, and respond to malware threats impacting organizational endpoints, ensuring compliance with global standards and supporting operational resilience.
Robust Endpoint Security
Enforces mandatory anti-malware controls and real-time protection across all endpoints.
Regulatory Alignment
Supports compliance with ISO/IEC 27001:2022, GDPR, NIS2, DORA, and COBIT 2019 requirements.
Centralized Monitoring
Requires integration of endpoint telemetry with SIEM for continuous visibility and rapid response.
Read Full Overview
Policy Diagram
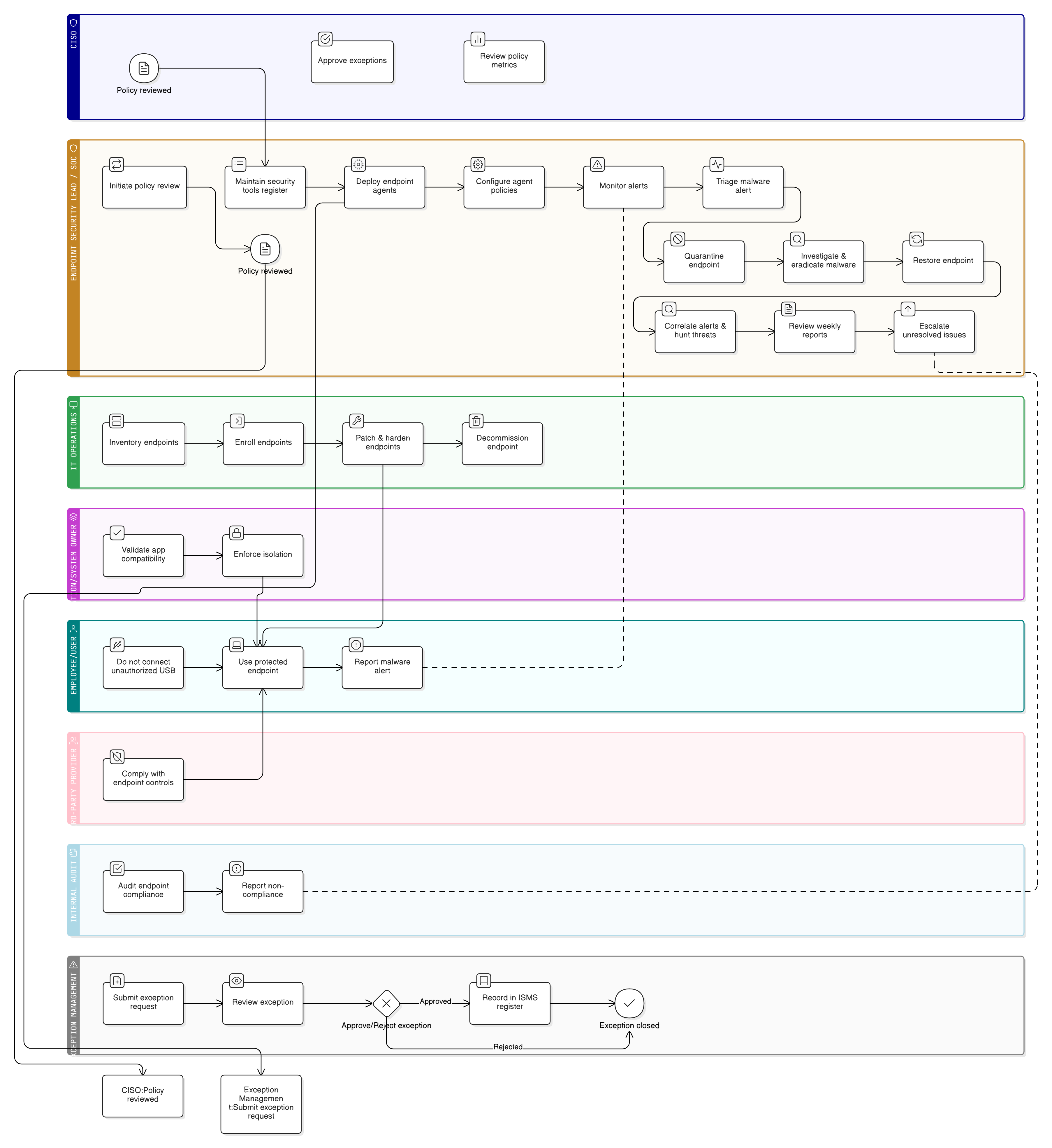
Click diagram to view full size
What's Inside
Scope and Mandatory Controls
Roles and Responsibilities
Technical & Governance Requirements
Malware Detection and Response Standards
Exception & Risk Treatment Process
Compliance and Review Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy
Establishes foundational principles for the protection of systems, data, and networks. This policy enforces those principles at the endpoint level through technical and procedural malware controls.
Access Control Policy
Defines user access restrictions which are enforced at the endpoint layer, including protections against privilege escalation and unauthorized installations of unvetted software.
Change Management Policy
Ensures that updates to endpoint protection software, policy rules, or agent configurations are subject to approval and controlled deployment processes.
Asset Management Policy
Provides the asset classification and inventory baseline required for endpoint visibility, patch coverage, and malware protection scope definition.
Logging And Monitoring Policy
Enables integration of endpoint alerts, agent health status, and threat intelligence into centralized SIEM systems for real-time detection and forensic traceability.
Incident Response Policy
Links endpoint-based malware incidents to standardized containment, eradication, investigation, and recovery workflows with assigned roles and escalation thresholds.
About Clarysec Policies - Endpoint Protection and Malware Policy
Effective security governance requires more than just words; it demands clarity, accountability, and a structure that scales with your organization. Generic templates often fail, creating ambiguity with long paragraphs and undefined roles. This policy is engineered to be the operational backbone of your security program. We assign responsibilities to the specific roles found in a modern enterprise, including the CISO, IT Security, and relevant committees, ensuring clear accountability. Every requirement is a uniquely numbered clause (e.g., 5.1.1, 5.1.2). This atomic structure makes the policy easy to implement, audit against specific controls, and safely customize without affecting document integrity, transforming it from a static document into a dynamic, actionable framework.
Clear Role Assignment
Precisely defines endpoint security responsibilities for CISO, SOC, IT Operations, users, and third-party providers.
Actionable Response Playbook
Includes a detailed incident playbook covering alert validation, containment, and recovery for malware events.
Exception Handling Process
Built-in framework for documenting, approving, and reviewing endpoint protection exceptions and residual risks.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
