Overview
This SME-adapted remote work policy sets out clear security, device, access, and monitoring requirements to ensure business information remains protected when staff work offsite. Featuring simplified governance for organizations without in-house IT, it aligns with major global compliance standards including ISO/IEC 27001:2022, GDPR, NIS2, and DORA.
Secure Off-Site Access
Protects business data when employees and contractors work from home, travel, or shared spaces.
Device & Data Controls
Mandates device security, encrypted connections, proper file storage, and physical safeguards.
Clear SME Roles
Adapts oversight and responsibilities for SMEs without dedicated IT or security teams.
Incident Ready
Covers prompt incident reporting, risk reviews, and termination of remote access when needed.
27001:2022 Compliant
Fully aligned with ISO/IEC 27001, GDPR, NIS2, DORA, COBIT, and more.
Read Full Overview
Policy Diagram
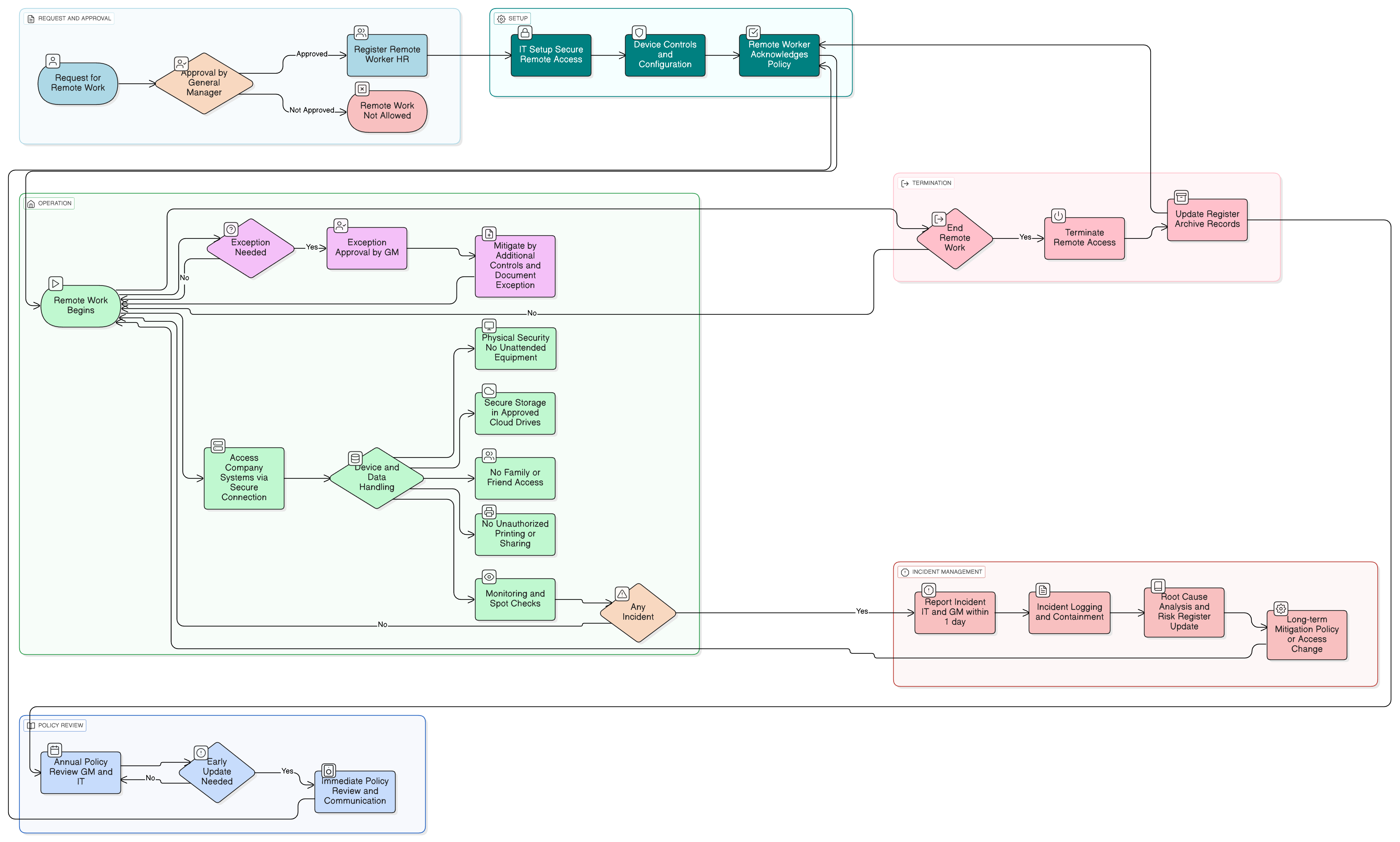
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Device Controls and Configuration
Governance for Remote Access
Data Handling and Physical Security
Incident Reporting and Monitoring
Risk and Exception Management
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Defines who authorizes and oversees remote access
Access Control Policy SME
Establishes secure remote access setup and revocation procedures
Risk Management Policy SME
Tracks and evaluates risks related to off-site access
Information Security Awareness And Training Policy SME
Trains users on remote work risks and best practices
Incident Response Policy SME
Manages response to remote access incidents such as credential leaks or device loss
About Clarysec Policies - Remote work policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Exception Handling Built-In
Temporary, approved remote work exceptions are safely documented and mitigated, no need for ad hoc workarounds.
Granular Compliance Enforcement
Every violation triggers action, with structured review, written warnings, or remote access removal; helps SMEs maintain standards.
Annual & Event-Driven Updates
Policy is proactively reviewed and updated for technology, law, or remote work incidents, keeping protections current.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
