Overview
This policy outlines structured audit and compliance monitoring processes for SMEs, ensuring controls, policies, and systems meet ISO 27001, GDPR, and legal obligations with minimal complexity.
SME-Ready Simplicity
Designed for SMEs with clear roles, repeatable checklists, and no need for a dedicated compliance team.
Standards-Based Auditing
Aligns with ISO 27001, GDPR, NIS2, DORA, NIST SP 800-53, and COBIT 2019 for proven compliance.
Full-Scope Review
Applies to all departments, systems, and third parties involved in IT, data, or critical services.
Structured Corrective Actions
Audit findings are documented, risk-rated, assigned, and tracked for reliable remediation.
Read Full Overview
Policy Diagram
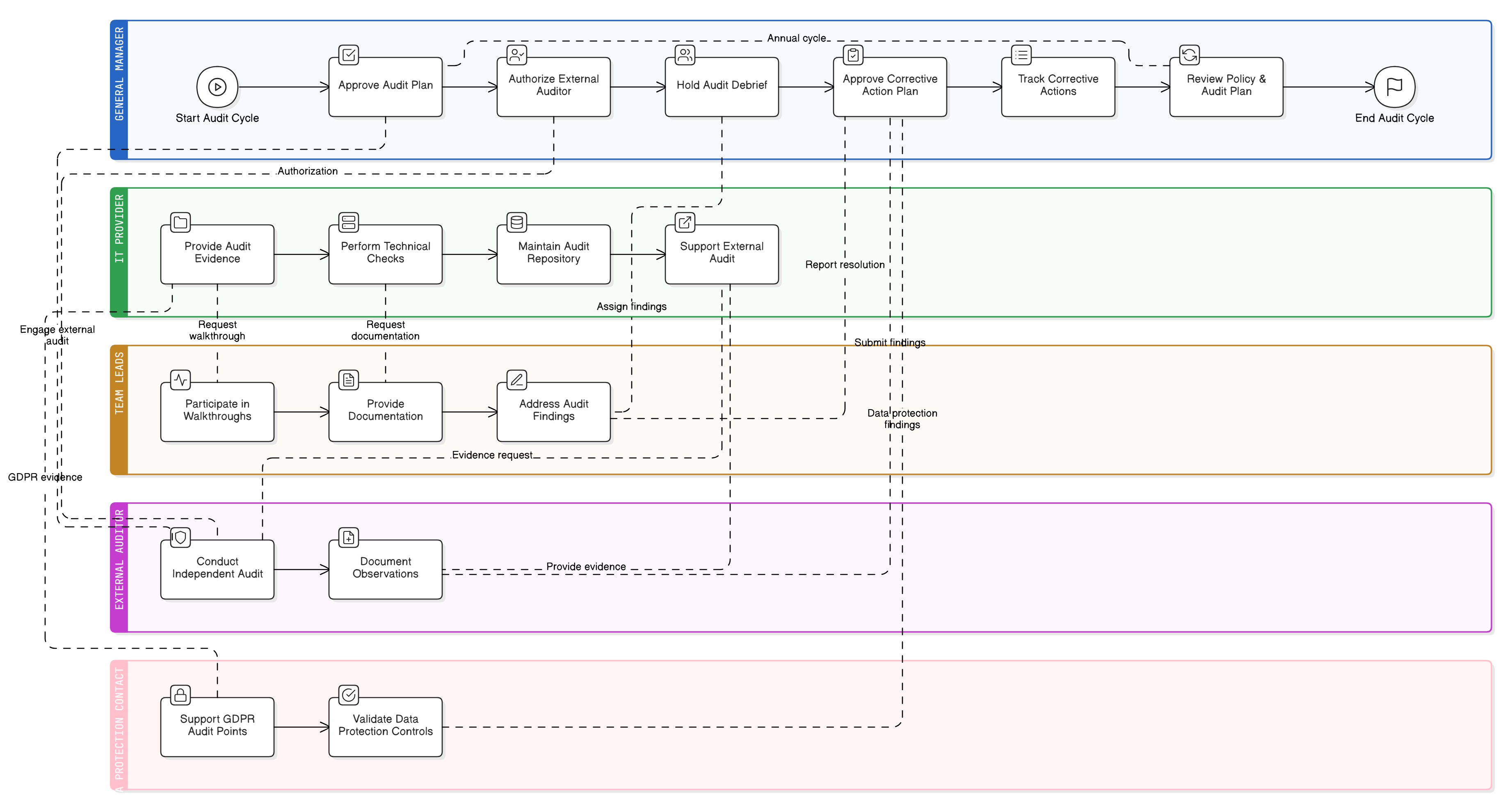
Click diagram to view full size
What's Inside
Scope and Annual Review Requirements
Structured Audit Checklists
Risk-Based Findings and Corrective Actions
Evidence Collection and Retention Rules
Legal, Regulatory, and Client Audit Coverage
SME-Specific Roles and Governance
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Information Security Policy-SME
Sets the baseline for all control expectations and requires enforcement through audits.
Governance Roles And Responsibilities Policy-SME
Establishes accountability for audit planning, execution, and corrective action ownership.
Risk Management Policy-SME
Identifies control weaknesses uncovered in audits and ensures that findings are documented in the risk register.
Data Protection And Privacy Policy-SME
Defines GDPR controls that must be audited, including data handling, breach response, and privacy notices.
Logging And Monitoring Policy-SME
Supplies the audit logs and forensic data used during compliance and control reviews.
Incident Response Policy-SME
Requires periodic audit of incident records and post-event reviews to verify response effectiveness.
Evidence Collection And Forensics Policy-SME
Provides the procedures for gathering verifiable, chain-of-custody evidence during audits.
About Clarysec Policies - Audit and Compliance Monitoring Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Centralized Evidence Management
All audit evidence is collected, organized, and retained in a single secure folder for smooth certification and client reviews.
Collaborative Audit Participation
Includes clear requirements for General Managers, IT Providers, and team leads to ensure full coverage and shared accountability.
Flexible Risk Exception Handling
Allows custom treatment and documentation of audit risks or scheduling gaps for real-world business constraints.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
