Overview
The Acceptable Use Policy (AUP) for SMEs defines responsible, secure IT use expectations for all personnel, including BYOD and third parties, ensuring data integrity, compliance, and accountability, with roles adapted for companies that lack dedicated IT teams.
Clear User Behavior Standards
Establishes enforceable rules for using company systems, safeguarding data and privacy.
Covers All Roles & Environments
Applies to employees, contractors, and third parties in any working scenario, including BYOD and remote work.
Ensures SME Compliance
Designed for SMEs without dedicated IT teams; roles suited for General Manager oversight and ISO 27001:2022 compliance.
Supports Data Integrity
Requires technical controls to prevent misuse and mandates clear incident reporting.
Read Full Overview
Policy Diagram
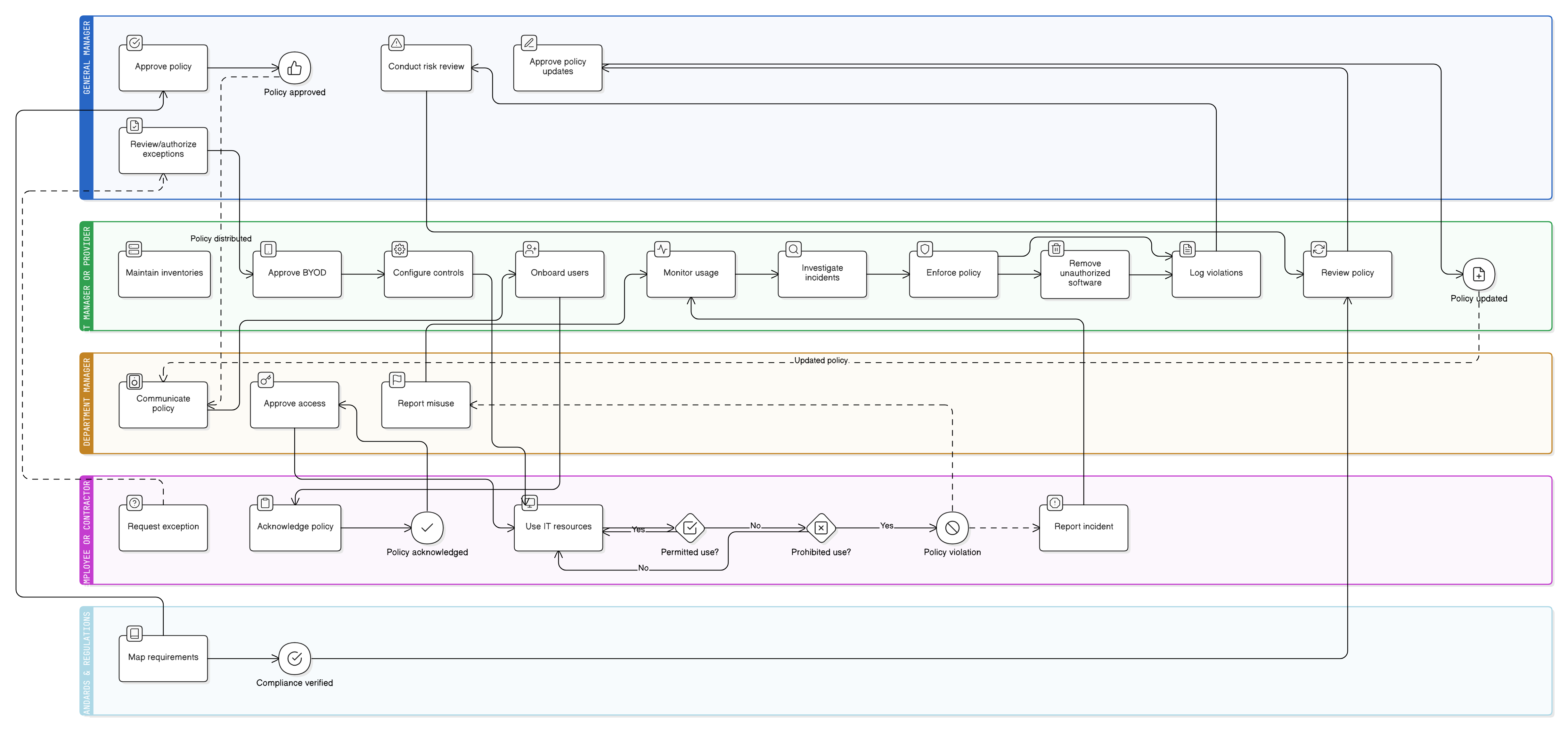
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Acceptable and Prohibited Use Definitions
BYOD Usage and Security Requirements
Roles for General Manager, IT, Employees
Monitoring, Enforcement, and Reporting
Annual Review and Exception Handling
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Access Control Policy-SME
Defines technical and procedural enforcement of permitted use and account restrictions.
Information Security Awareness And Training Policy-SME
Provides user education on acceptable use boundaries and reporting obligations.
Remote Work Policy-SME
Regulates use of company systems in offsite or home environments.
Data Protection And Privacy Policy-SME
Enforces personal data handling rules that intersect with acceptable use monitoring and BYOD.
Incident Response Policy-SME
Governs procedures for investigating and responding to misuse or violations of acceptable use terms.
About Clarysec Policies - Acceptable Use Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
BYOD Security Built-In
Pre-approval and strict controls for personal devices ensure business data stays protected regardless of ownership.
Atomic, Checklist Format
Numbered clauses turn requirements into actionable steps, no ambiguity or broad, hard-to-enforce statements.
Actionable Exception Handling
All exceptions require review, documentation, controls, and a clear expiry, minimizing security gaps from special cases.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
