Overview
This policy details clear, actionable requirements for user account and privilege management in SMEs. It mandates traceable, role-based access, periodic reviews, password standards, and formalized onboarding/offboarding. The General Manager assumes overall accountability, supported by the IT Lead, and all processes ensure compliance with ISO/IEC 27001, GDPR, NIS2, and more.
End-to-End Account Security
Covers the full lifecycle of user accounts, from creation to deactivation, ensuring all access is documented and traceable.
SME-tailored Roles & Simplicity
Delegates responsibilities to General Manager and IT Lead, suiting organizations without large IT teams.
Regulatory Compliance
Aligns with ISO/IEC 27001:2022, GDPR, NIS2, and DORA, ensuring compliance across multiple standards.
Principle of Least Privilege
Minimizes risk by enforcing only necessary access and mandatory approvals for elevated privileges.
Read Full Overview
Policy Diagram
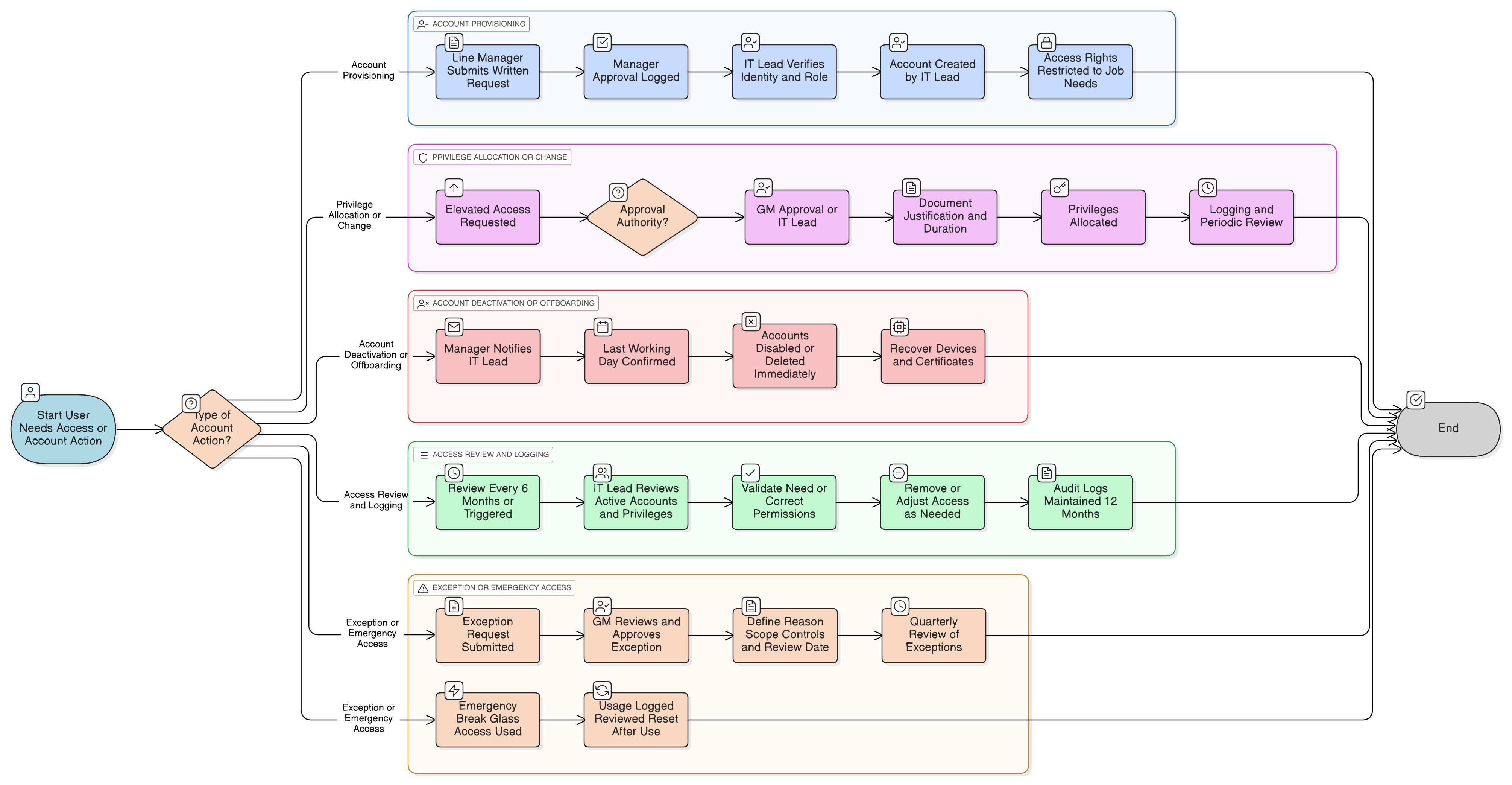
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Privileges and Access Control Requirements
Account Lifecycle Management
Password and MFA Requirements
Offboarding and Emergency Access
Risk Treatment and Exceptions
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 | |
| EU GDPR |
Article 32
|
Related Policies
Governance Roles And Responsibilities Policy-SME
Establishes accountability and decision-making authority for access approvals and oversight.
Access Control Policy-SME
Governs system-wide access control enforcement and authentication methods.
Onboarding And Termination Policy-SME
Ensures account creation and removal are built into HR-managed personnel changes.
Information Security Awareness And Training Policy-SME
Trains users on secure account practices and usage expectations.
Incident Response Policy-SME
Defines actions to be taken if account misuse leads to a security breach or unauthorized disclosure.
About Clarysec Policies - User Account and Privilege Management Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Audit-Ready Access Records
Retains detailed logs of all account activities and approvals for 12 months, simplifying regulatory audits and investigations.
Quarterly Exception Reviews
Ensures any special access (e.g., test or emergency) is strictly controlled, justified, and regularly re-assessed.
Seamless Offboarding Process
Integrates clear checklist steps for immediate account removal, device recovery, and certificate handling on staff departure.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
