Overview
The Cloud Usage Policy (P27S) defines how SMEs securely manage and govern cloud services, enforcing approval, access controls, compliance with major regulations, and ongoing monitoring, all with practical roles and responsibilities.
SME-Friendly Cloud Governance
Defines clear roles and responsibilities for cloud approvals, use, and monitoring, no dedicated IT teams required.
Mandatory Security Controls
Enforces MFA, strong passwords, activity logging, and access management for all approved cloud services.
Regulatory Compliance Built-In
Aligns with ISO/IEC 27001, GDPR, NIS2, and DORA for cloud service security, data residency, and supplier contracts.
Read Full Overview
Policy Diagram
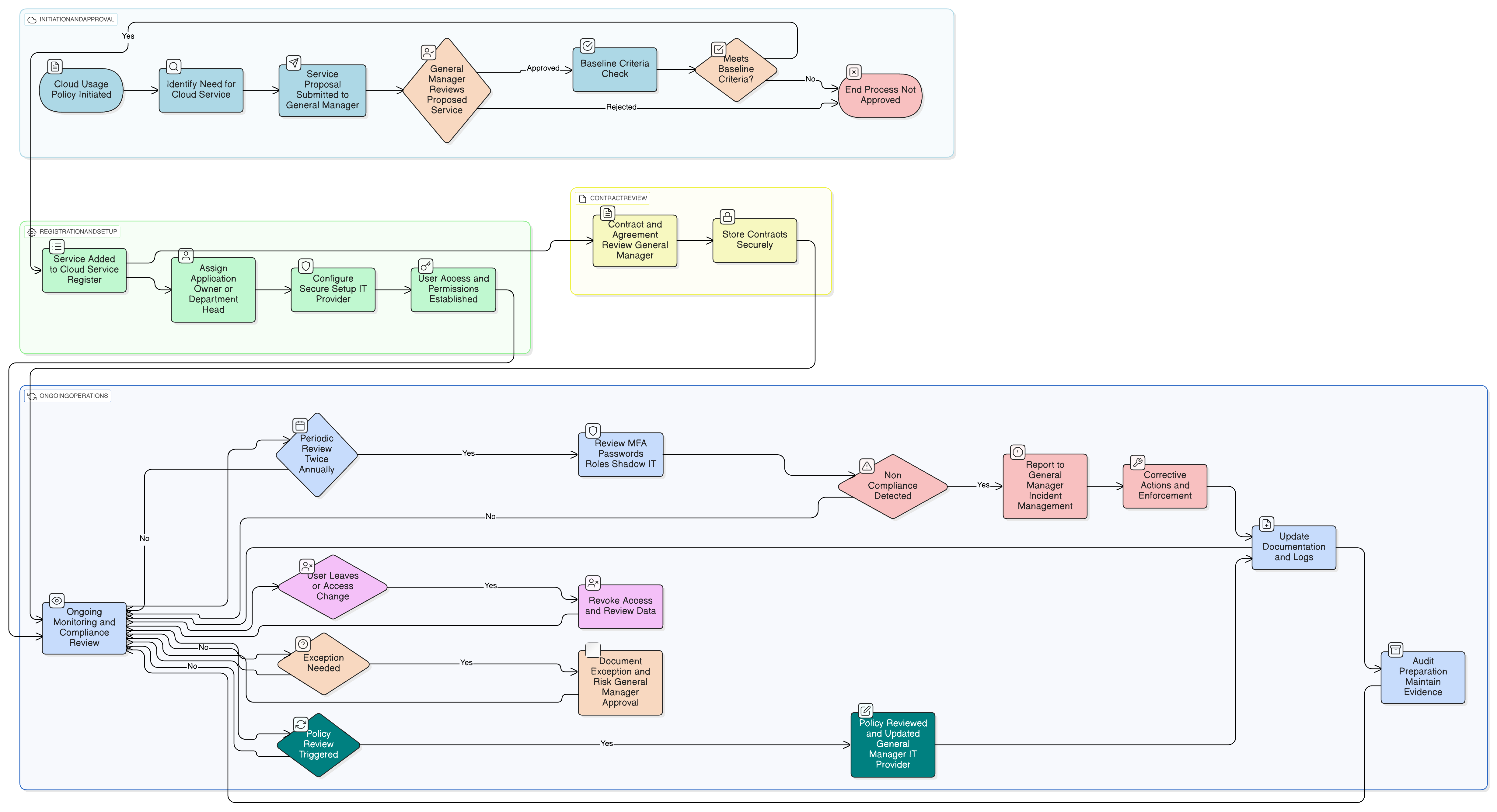
Click diagram to view full size
What's Inside
Scope and Roles for SME Cloud Usage
Cloud Service Register and Approval
Access Controls, MFA, and Password Requirements
Data Retention, Backup, and Exit Controls
Vendor Contracts and Regulatory Compliance
Monitoring, Review, and Policy Enforcement
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 28Article 32Chapter V
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Governance Roles And Responsibilities Policy-SME
Defines accountability for approving cloud services and managing provider relationships.
Access Control Policy-SME
Supports secure login, session management, and revocation practices required for cloud platforms.
Data Retention And Disposal Policy-SME
Governs how cloud-based data is backed up, retained, and deleted in accordance with legal obligations.
Data Protection And Privacy Policy-SME
Ensures any personal data stored in cloud services is handled according to GDPR principles.
Incident Response Policy-SME
Provides structured procedures for responding to cloud security incidents, including evidence collection and external notification.
About Clarysec Policies - Cloud Usage Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
All Cloud Services Tracked
A live Cloud Service Register lists every approved tool, who owns it, where data is stored, and renewal or support info.
Simple Exception Management
Provides clear steps for safely handling temporary or emergency cloud tool exceptions, with risk ratings and expiry dates.
Data Retention & Export Controls
Ensures that backup, export, and deletion procedures are in place for business-critical cloud data, preventing vendor lock-in.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
