Overview
This Time Synchronization Policy outlines organizational requirements for automated, accurate timekeeping across all systems, supporting audit, compliance, and incident response. It is tailored for SMEs, assigning responsibilities to General Manager and IT roles, and aligns with ISO 27001, GDPR, DORA, and NIS2.
Audit-Ready Logs
Automated time sync ensures logs remain accurate and defensible for audits and investigations.
Regulatory Compliance
Meets ISO 27001, GDPR, DORA, and NIS2 time accuracy requirements for operational integrity.
Comprehensive Device Coverage
Covers company-owned, BYOD, cloud, network, and remote systems for robust protection.
Read Full Overview
Policy Diagram
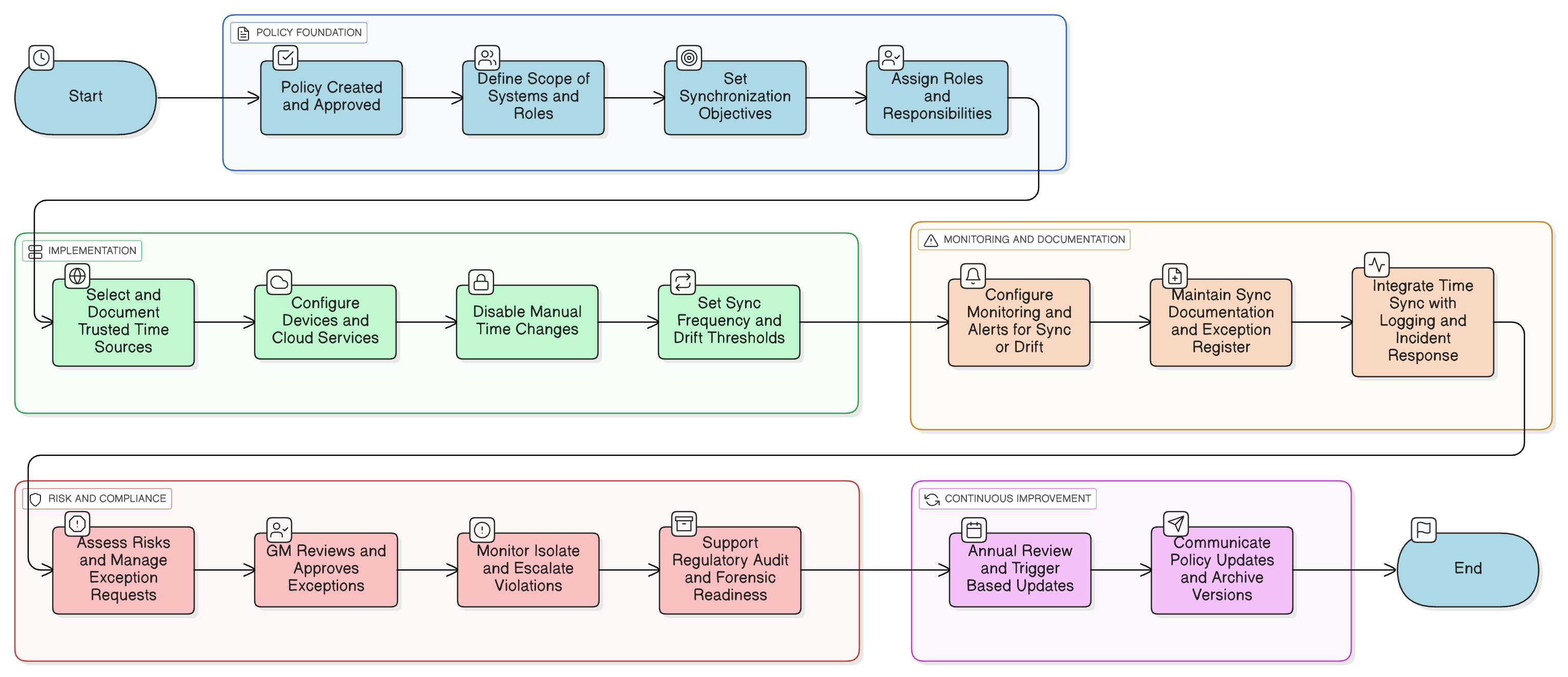
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles and Responsibilities (General Manager & IT)
Time Source Selection & NTP Standards
Monitoring and Alerting for Time Drift
Manual Override Controls & Exception Handling
Cloud Provider Sync Assurance
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Logging And Monitoring Policy-SME
Ensures consistent timestamping across logs for traceability and forensic correlation.
Incident Response Policy-SME
Relies on timestamp accuracy to reconstruct incidents, define timelines, and support notification decisions.
Data Protection And Privacy Policy-SME
Ensures that access logs and data handling timelines involving personal data are accurate and defensible under GDPR.
Asset Management Policy-SME
Supports identification of systems requiring synchronization, particularly mobile and remote devices.
Third Party And Supplier Security Policy-SME
Ensures vendors that access or log data for the organization follow synchronized time practices contractually.
About Clarysec Policies - Time Synchronization Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Real-Time Alerts for Time Drift
Automatic monitoring and instant alerts for any device with clock drift or sync failures, minimizing risk to business operations.
Practical Role Assignment
Defines responsibilities for GM, IT, and Privacy Officer, streamlining compliance steps, even for teams without security specialists.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
