Overview
This SME-focused Network Security Policy defines clear roles, controls, and technical requirements for securing all network components, ensuring compliance with ISO 27001:2022, GDPR, NIS2, and DORA. The policy is structured for organizations with simplified governance, assigning practical responsibilities to the General Manager and IT provider, and is audit-ready for regulatory demands.
Comprehensive Network Controls
Defines strict controls for wired, wireless, and cloud networks, safeguarding against unauthorized access and cyber threats.
Clear Roles for SMEs
Assigns network security responsibilities to the General Manager and IT provider, ideal for businesses without dedicated IT security teams.
Audit-Ready Compliance
Supports ISO 27001, GDPR, NIS2, and DORA requirements; structured for easy audit preparation and regulatory assurance.
Read Full Overview
Policy Diagram
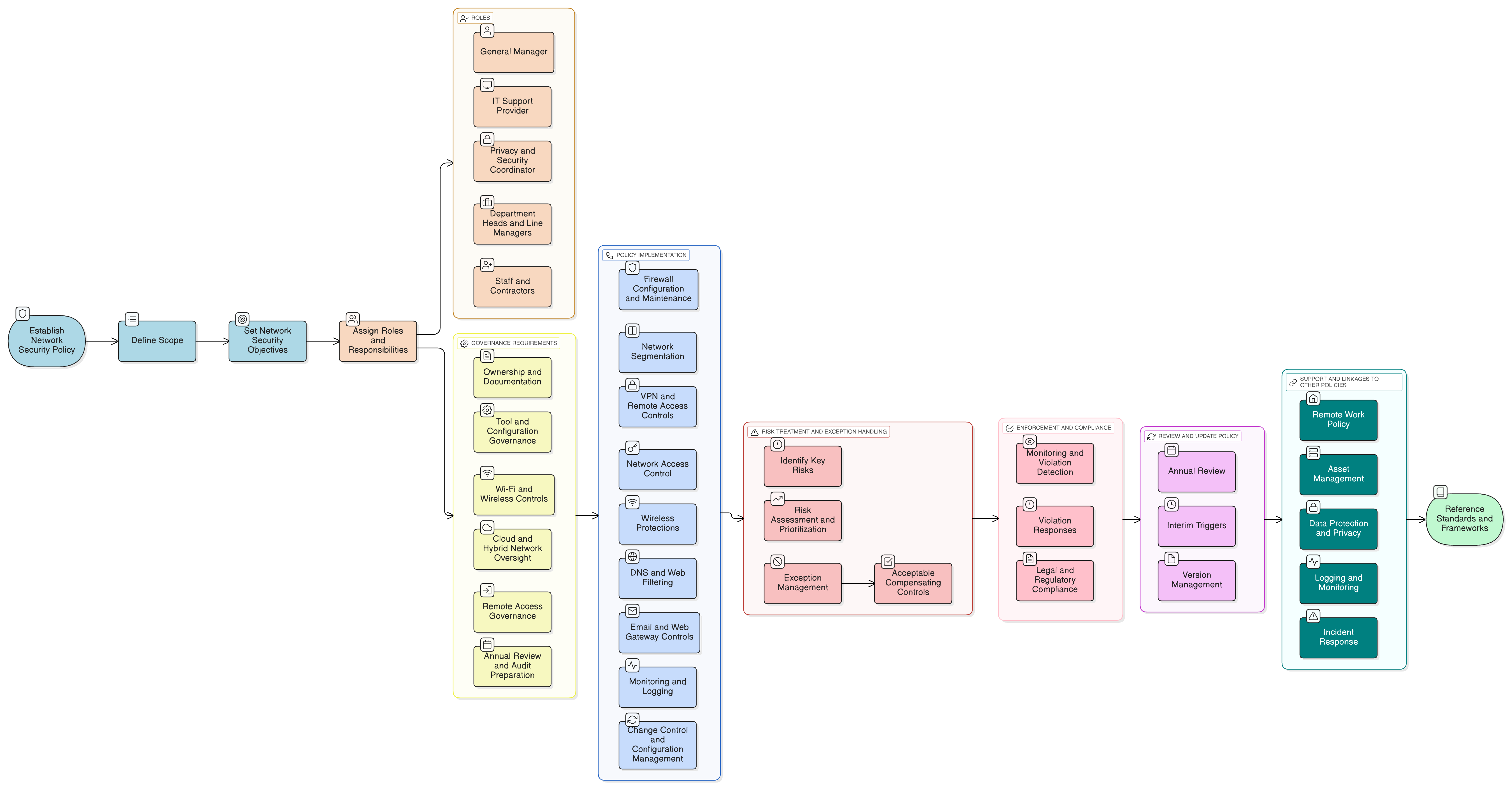
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Roles and Responsibilities for SMEs
Network Segmentation and Firewalls
Remote Access and VPN Controls
Annual Review and Audit Preparation
Exception and Compensating Controls Management
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
| Framework | Covered Clauses / Controls |
|---|---|
| ISO/IEC 27001:2022 | |
| ISO/IEC 27002:2022 | |
| NIST SP 800-53 Rev.5 | |
| EU GDPR |
Article 32
|
| EU NIS2 | |
| EU DORA | |
| COBIT 2019 |
Related Policies
Remote Work Policy-SME
Enforces secure remote access methods, VPN requirements, and endpoint protection for off-site users.
Asset Management Policy-SME
Ensures all network-connected systems are identified, categorized, and tracked with up-to-date security statuses.
Data Protection And Privacy Policy-SME
Ensures that network segmentation, access controls, and logging support privacy and data protection principles under GDPR.
Logging And Monitoring Policy-SME
Specifies requirements for capturing and reviewing logs from network devices, remote connections, and wireless controllers.
Incident Response Policy-SME
Defines required actions in response to network breaches, unauthorized access attempts, or malware propagation via internal networks.
About Clarysec Policies - Network Security Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Segmented Network Protection
Reduces malware spread and insider risks by enforcing strong segmentation between internal, guest, and IoT networks.
Granular Exception Workflow
Features a uniquely detailed exception process, documented, time-limited, and linked to compensating controls for audit clarity.
Integrated Change Management
Every network change follows a documented process, with emergency updates reviewed, logged, and securely backed up monthly.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
