Overview
This policy sets out clear, SME-friendly requirements for protecting all endpoint devices, including BYOD and mobile, from malware, supporting compliance with ISO 27001:2022, GDPR, and related standards. It assigns responsibilities to the General Manager and IT providers, details controls for prevention, detection, response, documentation, and awareness, and is tailored for organizations without dedicated cybersecurity teams.
Comprehensive Endpoint Security
Protects all organizational and personal devices from malware, including laptops, mobiles, and portable media.
Clear Roles for SMEs
Simplified responsibilities for General Managers and IT providers ensure policy compliance in small business settings.
Regulatory Alignment
Supports ISO/IEC 27001:2022, GDPR, NIS2, and DORA compliance through robust malware controls.
BYOD & Remote Work Coverage
Applies to both company-owned and personally owned devices, supporting hybrid and remote workforces.
Read Full Overview
Policy Diagram
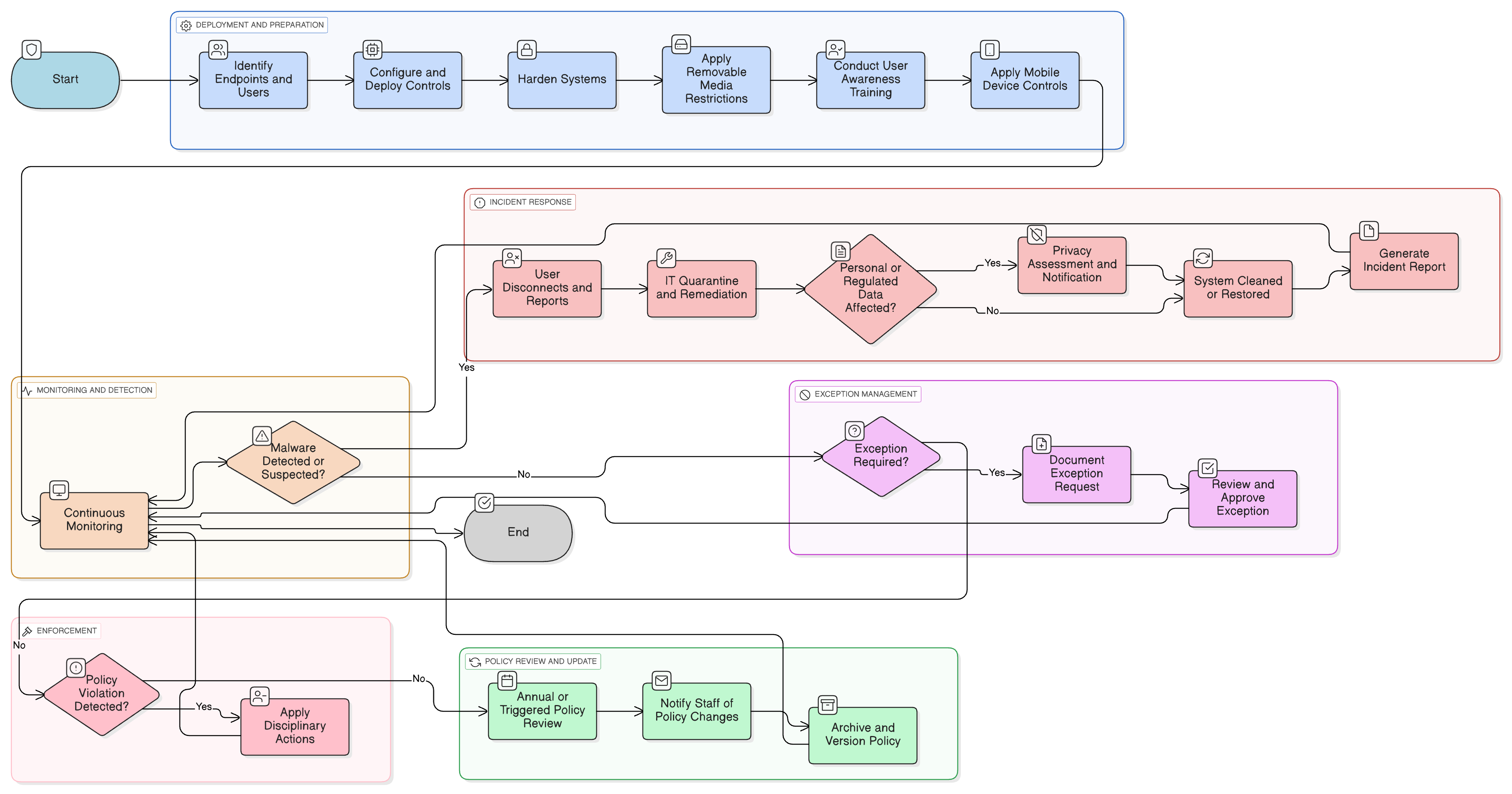
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
BYOD and Mobile Device Controls
Incident Response and Reporting
Audit and Logging Requirements
Malware Awareness Training
Device Encryption and Hardening
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Remote Work Policy-SME
Ensures endpoint protection requirements are enforced on devices used off-site or in hybrid settings.
Asset Management Policy-SME
Supports tracking and control over all endpoints, ensuring only authorized and protected devices are used.
Data Protection And Privacy Policy-SME
Reinforces malware prevention as a core privacy control to protect personal and sensitive data from compromise.
Logging And Monitoring Policy-SME
Establishes the requirements for logging malware events and maintaining alert visibility for early response.
Incident Response Policy-SME
Defines escalation, containment, and external notification steps if malware leads to data compromise or operational disruption.
About Clarysec Policies - Endpoint Protection and Malware Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Automated Malware Detection & Response
Uses real-time scans, automated quarantines, and incident reporting to contain threats and restore devices quickly.
Built-In Staff Training & Awareness
Mandates ongoing user awareness, simulated phishing, and reporting to reduce malware risk from user mistakes.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
