Overview
The P16S Data Masking and Pseudonymization Policy sets clear, enforceable requirements for SMEs to protect sensitive data using approved masking and pseudonymization methods, ensuring compliance with global standards and legal mandates.
Mandatory Data Transformation
Enforces masking or pseudonymization for sensitive data in non-production, analytics, or third-party contexts.
SME-Friendly Roles
Clear General Manager ownership and roles tailored for organizations without dedicated IT security teams.
Compliance-Driven Framework
Aligns with ISO/IEC 27001:2022, GDPR, NIS2, DORA, and industry best practices to support certification and due diligence.
Read Full Overview
Policy Diagram
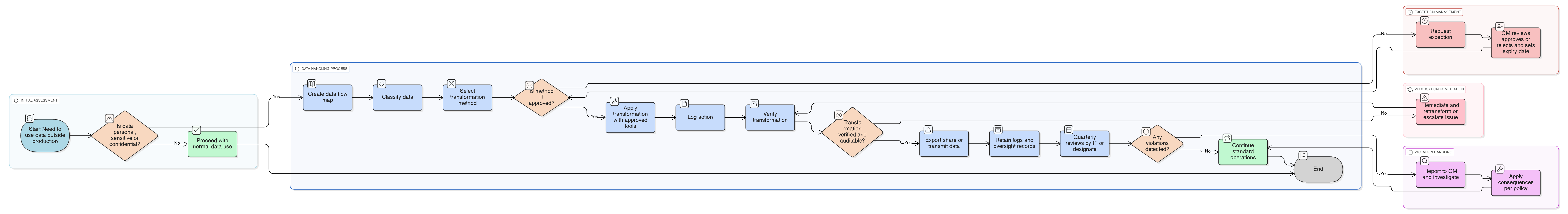
Click diagram to view full size
What's Inside
Scope and Rules of Engagement
Role-Based Transformation Responsibilities
Detailed Tool and Method Requirements
Exception and Risk Assessment Process
Audit, Logging, and Monitoring
Compliance and Review Procedures
Framework Compliance
🛡️ Supported Standards & Frameworks
This product is aligned with the following compliance frameworks, with detailed clause and control mappings.
Related Policies
Governance Roles And Responsibilities Policy-SME
Assigns overall accountability for policy implementation, risk acceptance, and exceptions approval.
Data Classification And Labeling Policy-SME
Defines the classification levels that determine when masking or pseudonymization must be applied.
Data Retention And Disposal Policy-SME
Ensures that transformed data sets, including backups, are retained and disposed of according to applicable rules.
Data Protection And Privacy Policy-SME
Aligns transformation practices with broader privacy obligations, including GDPR requirements.
Incident Response Policy-SME
Covers reporting and escalation procedures in the event of unauthorized data disclosure.
About Clarysec Policies - Data Masking and Pseudonymization Policy - SME
Generic security policies are often built for large corporations, leaving small businesses struggling to apply complex rules and undefined roles. This policy is different. Our SME policies are designed from the ground up for practical implementation in organizations without dedicated security teams. We assign responsibilities to the roles you actually have, like the General Manager and your IT Provider, not an army of specialists you don't. Every requirement is broken down into a uniquely numbered clause (e.g., 5.2.1, 5.2.2). This turns the policy into a clear, step-by-step checklist, making it easy to implement, audit, and customize without rewriting entire sections.
Full Auditability & Logging
Requires traceable logs for all masking, pseudonymization, key use, and exceptions, supporting easy audits and accountability.
Safe Exception Handling
Exceptions to standard data transformation must follow a documented, risk-based approval process with built-in review dates.
Format-Preserving Controls
Masked or pseudonymized data keeps original format to avoid system errors in test, development, and analytics environments.
Frequently Asked Questions
Built for Leaders, By Leaders
This policy was authored by a security leader with 25+ years of experience deploying and auditing ISMS frameworks for global enterprises. It's designed not just to be a document, but a defensible framework that stands up to auditor scrutiny.
